Category: writeup
-
 May 3, 2021FCSC 2021 - Intro - bofbof
May 3, 2021FCSC 2021 - Intro - bofbof
This challenge will cover a basic stack buffer overflow on the bofbof challenge of the France CyberSecurity Challenge (FCSC) 2021May 3, 2021 FCSC 2021 - Intro - bofbof -
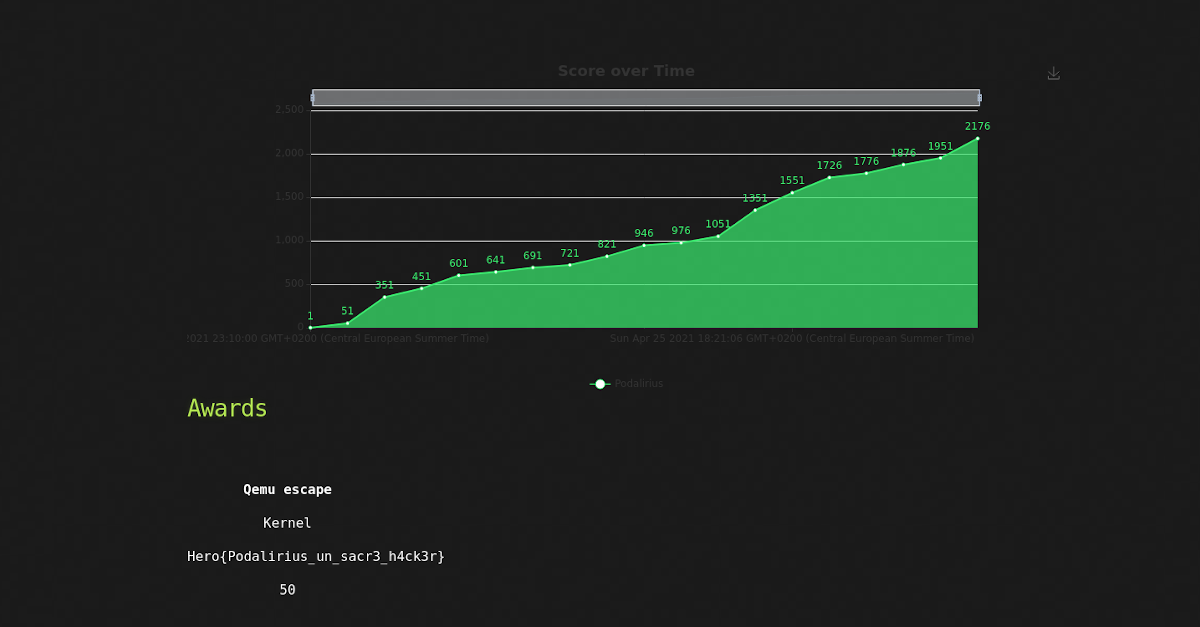
 May 3, 2021FCSC 2021 - Intro - Bonus Points
May 3, 2021FCSC 2021 - Intro - Bonus Points
In this challenge you will discover and exploit the unsigned integer overflow vulnerability, to set an arbitrary score in this service.May 3, 2021 FCSC 2021 - Intro - Bonus Points -
 May 3, 2021FCSC 2021 - Intro - Known Plaintext
May 3, 2021FCSC 2021 - Intro - Known Plaintext
In this challenge, you will perform an analysis of this XOR cryptosystem to decipher the flagMay 3, 2021 FCSC 2021 - Intro - Known Plaintext -
 May 3, 2021FCSC 2021 - Intro - Dérèglement
May 3, 2021FCSC 2021 - Intro - Dérèglement
This forensics challenge addresses the DOCX file format, in which a flag is hidden in plaintext.May 3, 2021 FCSC 2021 - Intro - Dérèglement -
 May 3, 2021FCSC 2021 - Intro - File format
May 3, 2021FCSC 2021 - Intro - File format
This challenge will teach you the basics of the IQ file format, used to save radio frequencies signal captures.May 3, 2021 FCSC 2021 - Intro - File format -
 May 3, 2021FCSC 2021 - Intro - guessy
May 3, 2021FCSC 2021 - Intro - guessy
In this challenge you will learn how to reverse a basic crackme with several basic validation steps.May 3, 2021 FCSC 2021 - Intro - guessy -
 May 3, 2021FCSC 2021 - Intro - La PIN
May 3, 2021FCSC 2021 - Intro - La PIN
This challenge focuses on a weak python script using AES GCM for encrypting the flag.May 3, 2021 FCSC 2021 - Intro - La PIN -
 May 3, 2021FCSC 2021 - Intro - Push it to the limit
May 3, 2021FCSC 2021 - Intro - Push it to the limit
This web application is vulnerable to an SQL injection in the login page. We will exploit it to bypass the authentication page and extract the administrator password.May 3, 2021 FCSC 2021 - Intro - Push it to the limit -
 May 3, 2021FCSC 2021 - Intro - Random Search
May 3, 2021FCSC 2021 - Intro - Random Search
This web application allow us to perform a Stored Cross Site Scripting (XSS) attack. We will use it to retrieve cookies from the administrator and get the flag.May 3, 2021 FCSC 2021 - Intro - Random Search -
 May 3, 2021FCSC 2021 - Intro - Rituel du Boutisme
May 3, 2021FCSC 2021 - Intro - Rituel du Boutisme
In this forensics challenge we need to find a flag in a disk image. We will need to change the endianness to read the flag with strings.May 3, 2021 FCSC 2021 - Intro - Rituel du Boutisme -
 May 3, 2021FCSC 2021 - Intro - Rituel en Chaine
May 3, 2021FCSC 2021 - Intro - Rituel en Chaine
In this forensics challenge, we need to find a flag in a disk image. To do this, we'll use the powerful strings command.May 3, 2021 FCSC 2021 - Intro - Rituel en Chaine -
 May 3, 2021FCSC 2021 - Intro - Snake
May 3, 2021FCSC 2021 - Intro - Snake
This challenge gives us access to a python interpreter and asks us to read the flag.txt. We will read the file, and for fun, open a shell afterwards.May 3, 2021 FCSC 2021 - Intro - Snake -
 May 3, 2021FCSC 2021 - Intro - Waterfall
May 3, 2021FCSC 2021 - Intro - Waterfall
A flag was hidden in the spectrogram of this signal. We will open the IQ file and display it as a waterfall to get it !May 3, 2021 FCSC 2021 - Intro - Waterfall -
 April 26, 2021HeroCTF 2021 - DevOps Box writeup
April 26, 2021HeroCTF 2021 - DevOps Box writeup
In this challenge, we will attack a DevOps Box, in various steps. We will exploit a Jenkins server to get a user reverse shell and privilege escalation to root using ansible.April 26, 2021 HeroCTF 2021 - DevOps Box writeup -
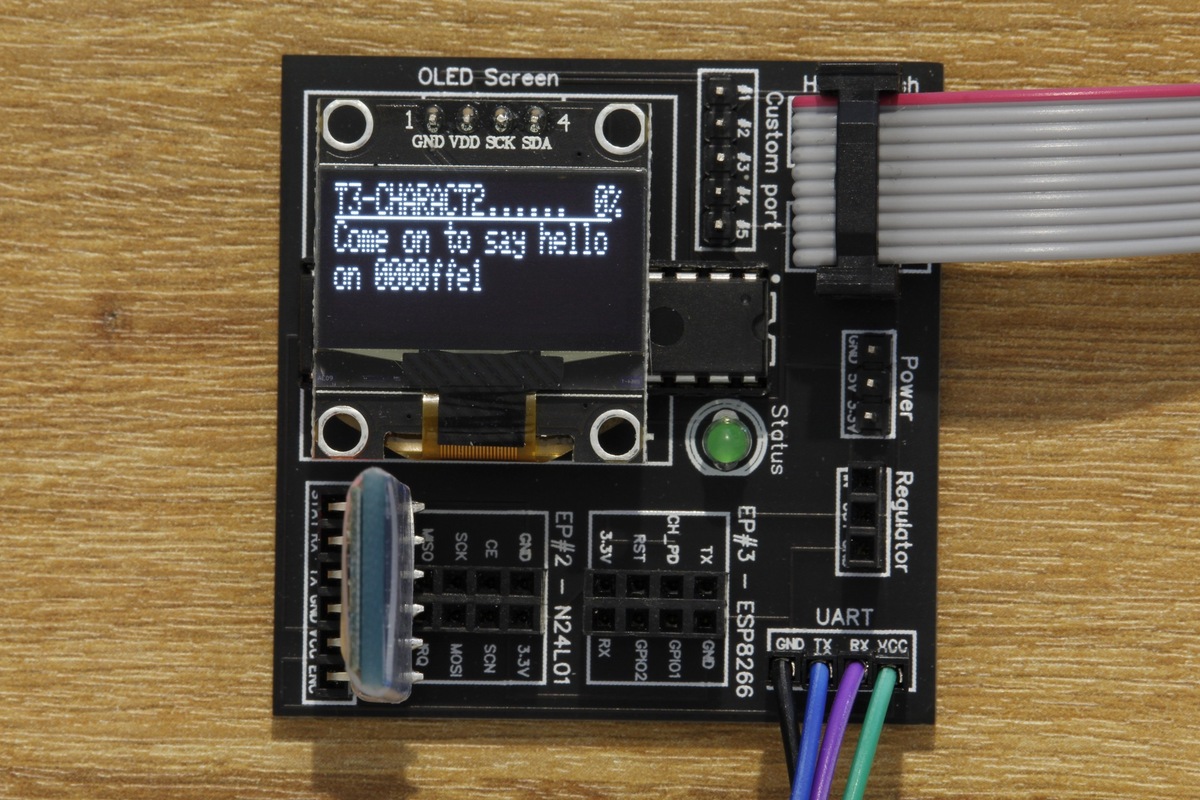 January 25, 2021DVID Writeup 06 - Bluetooth - Characteristics 2
January 25, 2021DVID Writeup 06 - Bluetooth - Characteristics 2
This challenge focuses on Bluetooth Low Energy characteristics for IoT devices.January 25, 2021 DVID Writeup 06 - Bluetooth - Characteristics 2 -
 January 25, 2021DVID Writeup 05 - Bluetooth - Characteristics
January 25, 2021DVID Writeup 05 - Bluetooth - Characteristics
This challenge focuses on Bluetooth Low Energy characteristics for IoT devices.January 25, 2021 DVID Writeup 05 - Bluetooth - Characteristics -
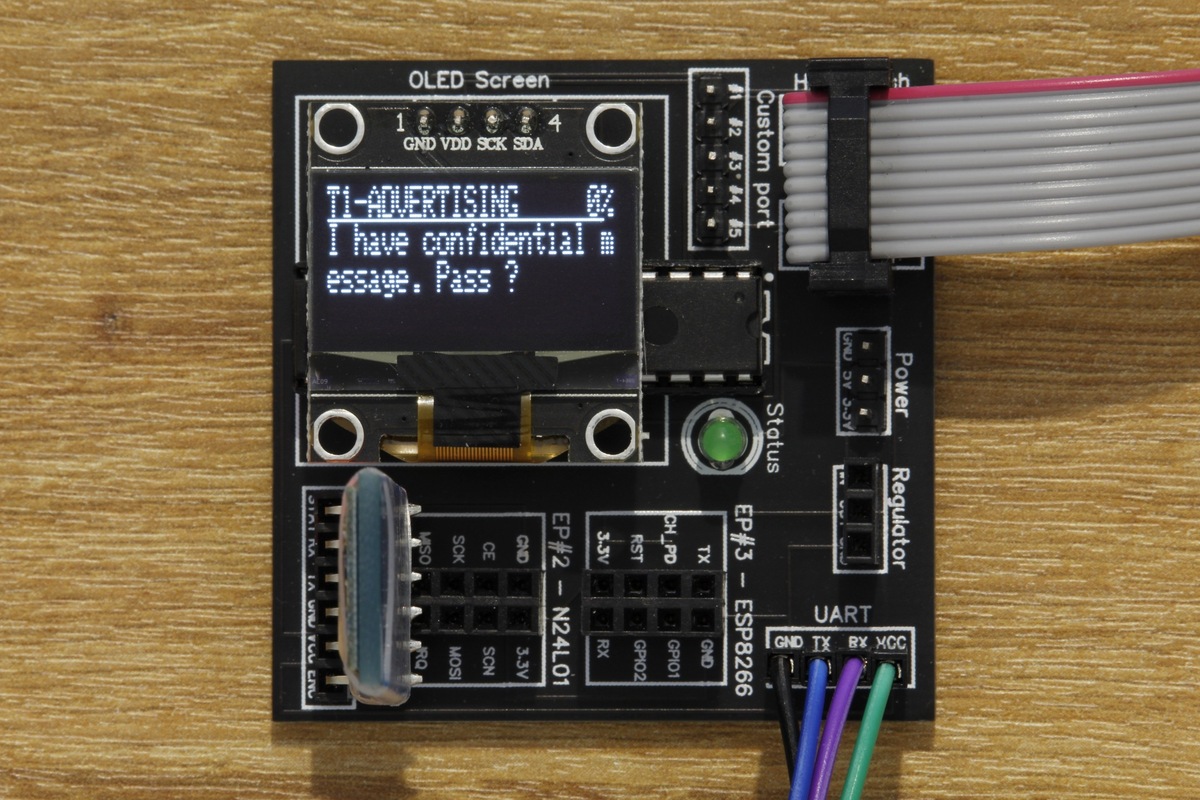
 January 25, 2021DVID Writeup 04 - Bluetooth - Advertising
January 25, 2021DVID Writeup 04 - Bluetooth - Advertising
This challenge focuses on the advertising phase of Bluetooth Low Energy for IoT devices.January 25, 2021 DVID Writeup 04 - Bluetooth - Advertising -
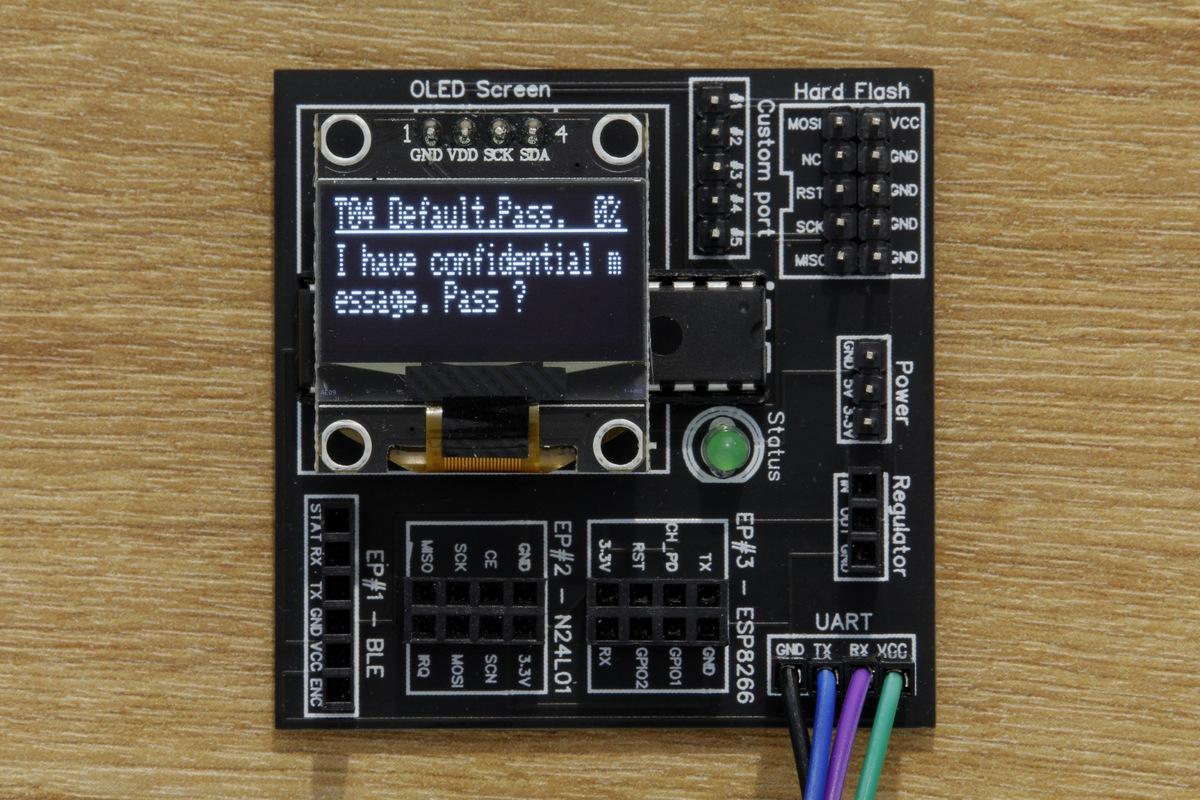 January 25, 2021DVID Writeup 03 - Firmware - Default password
January 25, 2021DVID Writeup 03 - Firmware - Default password
In this challenge, you will learn about the dangers of default passwords in IoT devicesJanuary 25, 2021 DVID Writeup 03 - Firmware - Default password
Compact view