DVID Writeup 04 - Bluetooth - Advertising
If you’re not yet familiar with the Damn Vulnerable Iot Device (DVID) project, I encourage you to read the project presentation page.
Goal of this challenge
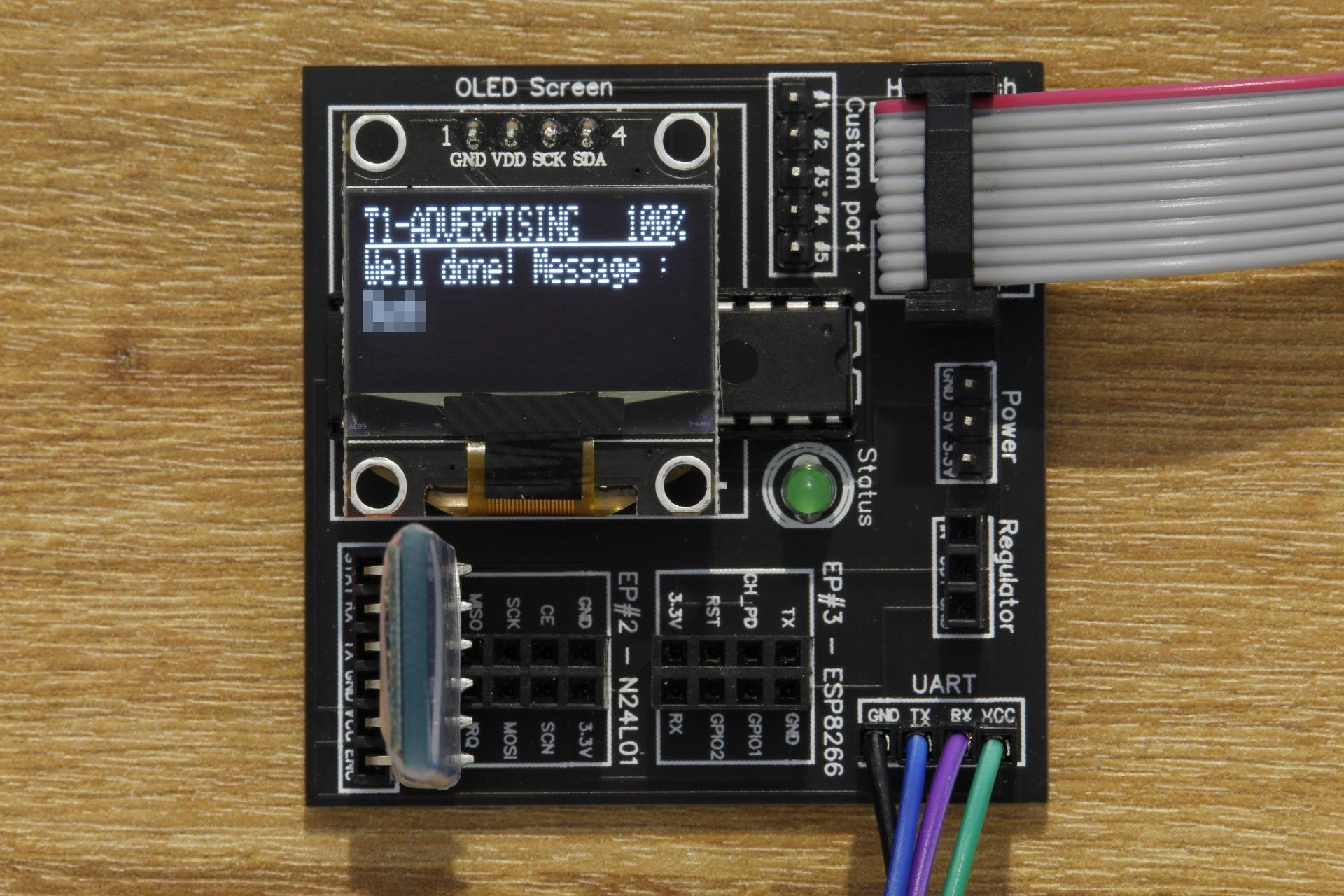
The bluetooth device name is advertised, find it and send it to the DVID board over UART !
Flashing the board
First things first, we are going to flash the firmware for this challenge onto the DVID board. In order to do this, we will use avrdude and an USB AVR programmer. If you’re not familiar with avrdude options I encourage you to read the flashing the board section of the first DVID writeup of this series. We will flash the board using this nice flash.sh script :
#!/bin/bash
if [[ ! -d "./DVID/" ]]; then
git clone https://github.com/vulcainreo/DVID
fi
pushd ./DVID/trainings/firmware/defaultPassword/
avrdude -F -v -p atmega328p -P /dev/ttyUSB0 -c usbasp -u -U flash:w:defaultPassword.ino.with_bootloader.arduino_standard.hex
popd
Now, we will connect the DVID board to our computer using the USB AVR programmer, and start the script. When the AVR programming has completed, the board should restart and you should see this :
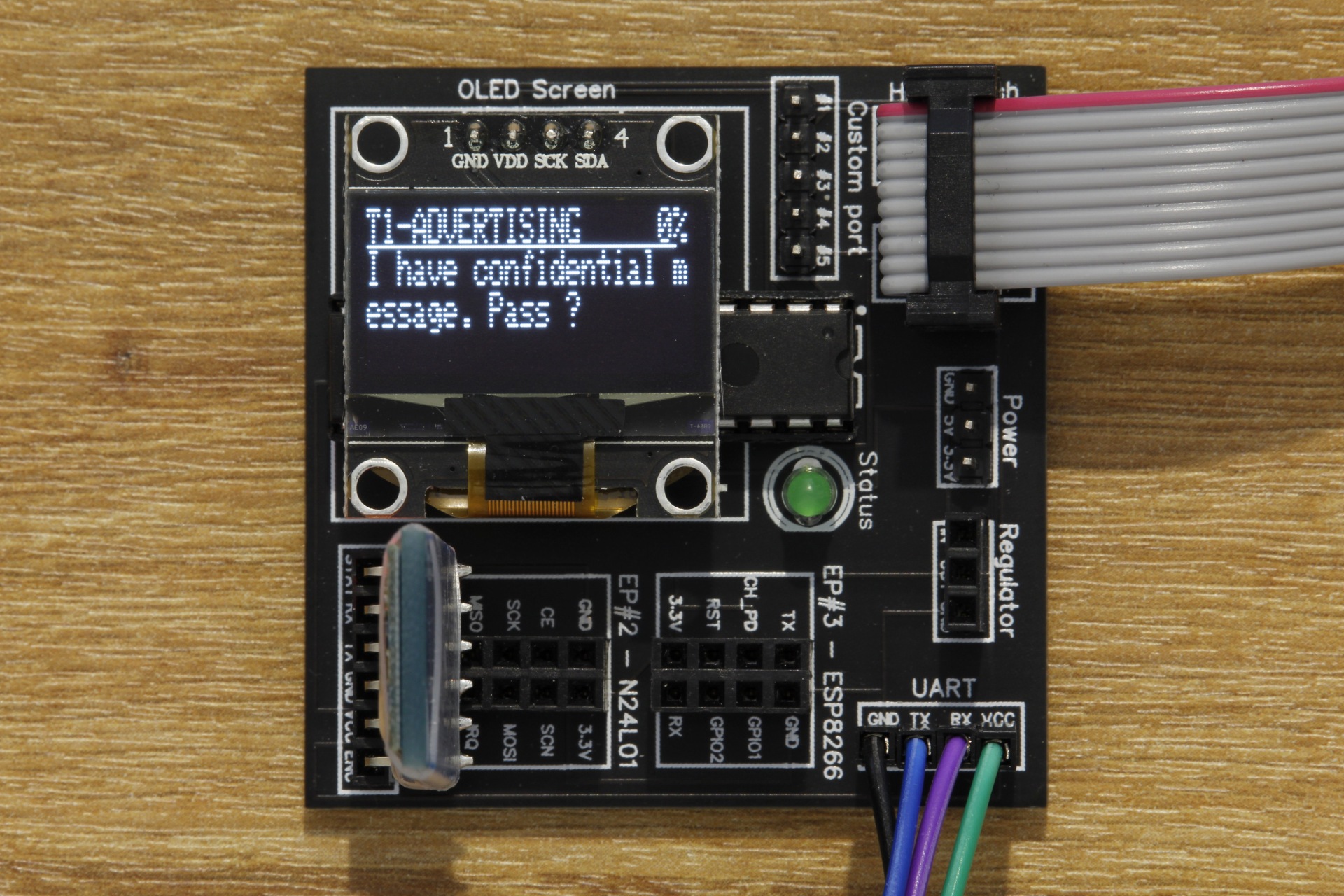
Solving the challenge
The DVID board is advertising its bluetooth address and name. To read it, we can either use a phone or bluetooth discovery service, or we can use bluetoothctl command :
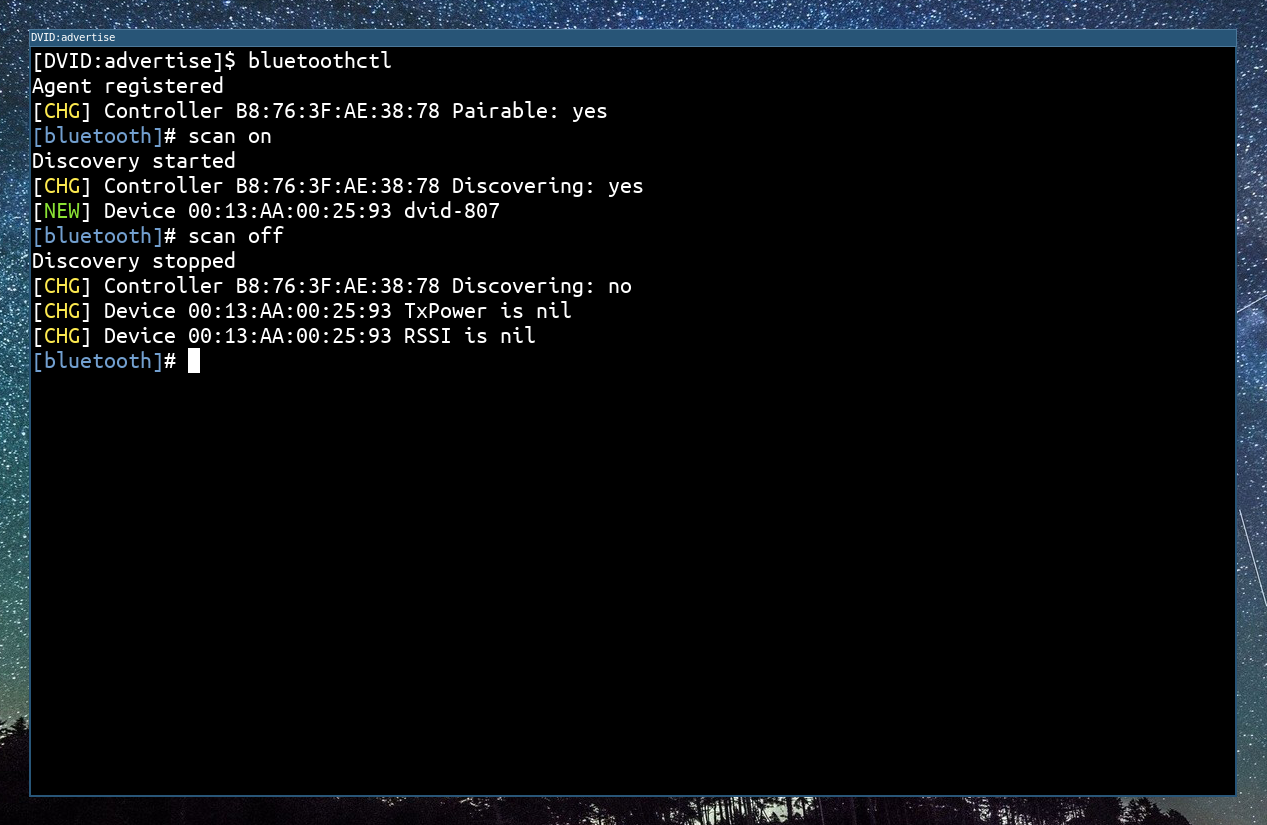
In the bluetooth advertising data, we find :
- The bluetooth address :
00:13:AA:00:25:93 - The device name :
dvid-807
Now that we have the device name dvid-807, we can send it over UART using this script :
#!/usr/bin/env python3
import serial
ser = serial.Serial("/dev/ttyUSB0", 9600)
ser.write(b'dvid-807\r\n')
And we win !