Category: poc
-
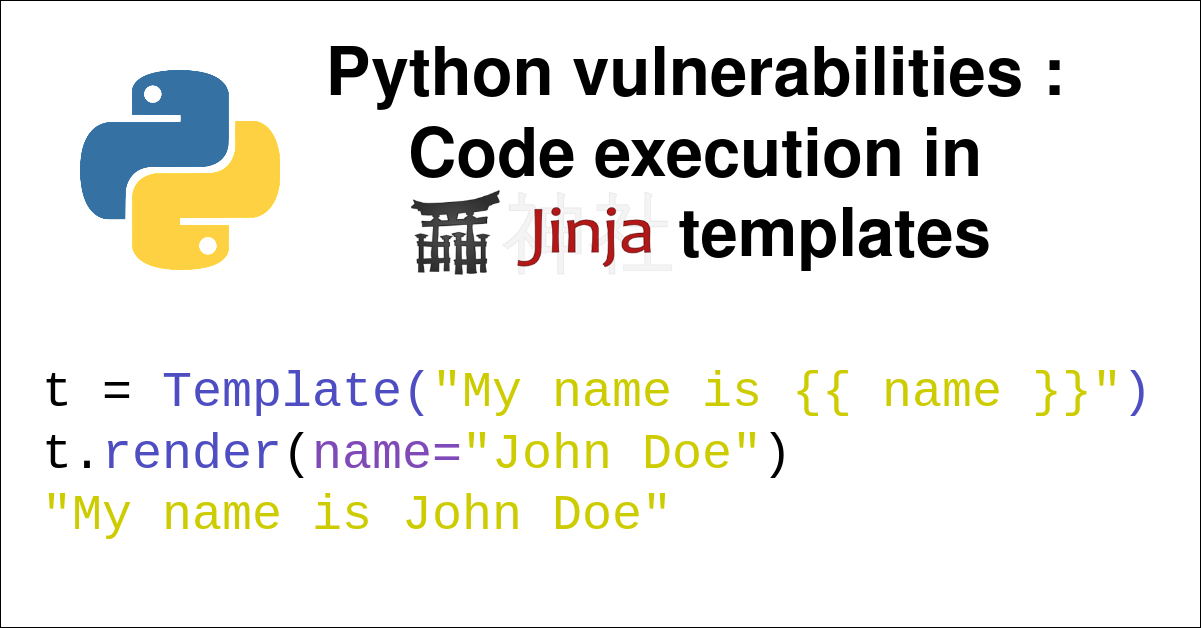 July 27, 2022Python vulnerabilities : Code execution in jinja templates
July 27, 2022Python vulnerabilities : Code execution in jinja templates
We will see how to create context-free payloads for jinja2, always allowing direct access to the os module in a jinja2 template without requirements. These payloads will be particularly useful for exploiting SSTI vulnerabilities. -
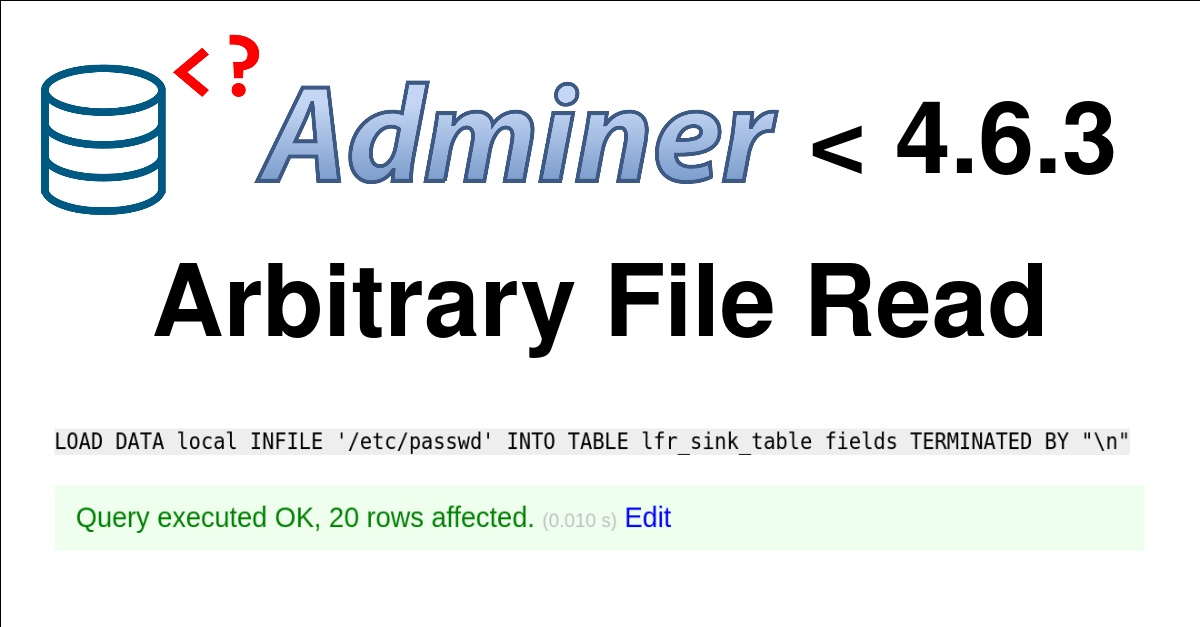 December 12, 2021Exploiting Adminer's file read vulnerability with LOCAL DATA
December 12, 2021Exploiting Adminer's file read vulnerability with LOCAL DATA
Improper Access Control in Adminer versions <= 4.6.2 (fixed in version 4.6.3) allows an attacker to achieve Arbitrary File Read on the server by connecting a remote MySQL database to the Adminer.December 12, 2021 Exploiting Adminer's file read vulnerability with LOCAL DATA -
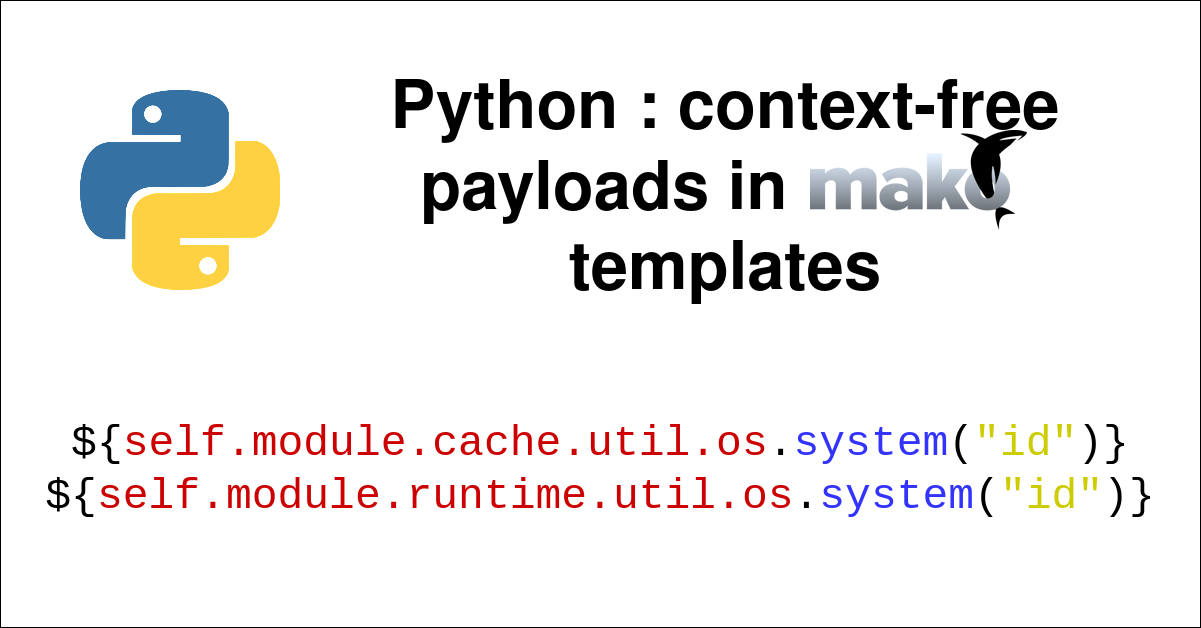 August 26, 2021Python context free payloads in Mako templates
August 26, 2021Python context free payloads in Mako templates
We will see how to create context-free payloads for Mako, always allowing direct access to the os module in a jinja2 template without requirements. These payloads will be particularly useful for exploiting SSTI vulnerabilities.August 26, 2021 Python context free payloads in Mako templates -
 July 27, 2021Python vulnerabilities : Code execution in jinja templates
July 27, 2021Python vulnerabilities : Code execution in jinja templates
We will see how to create context-free payloads for jinja2, always allowing direct access to the os module in a jinja2 template without requirements. These payloads will be particularly useful for exploiting SSTI vulnerabilities. -
 March 24, 2021Python format string vulnerabilities
March 24, 2021Python format string vulnerabilities
Python format strings can be very useful but they can be prone to vulnerabilities when misused.March 24, 2021 Python format string vulnerabilities -
 November 12, 2020Constructing a semi-interactive reverse shell with curl
November 12, 2020Constructing a semi-interactive reverse shell with curl
This article details how I created a curl-based reverse shell, from scratch.November 12, 2020 Constructing a semi-interactive reverse shell with curl -
 November 11, 2020Constructing a semi-interactive reverse shell with wget
November 11, 2020Constructing a semi-interactive reverse shell with wget
This article details how I created a wget-based reverse shell, from scratch.November 11, 2020 Constructing a semi-interactive reverse shell with wget
Compact view