Writing an exploit for RemoteMouse 3.008
Introduction
The RemoteMouse application is a program for remotely controlling a computer from a phone or tablet.

Reverse engineering of RemoteMouse version 3.008
In order to reverse engineer this program written in .NET, I opened it in the software dnSpy allowing to decompile with great accuracy .NET binaries.
Connexion au service
While looking for the functions managing the network in the decompiled code, we find this snippet quite quickly:
try {
this.tl = new TcpListener(IPAddress.Parse("0.0.0.0"), 1978);
this.tl.Server.NoDelay = true;
this.tl.Start();
} catch {
MessageBox.Show("Remote Mouse's port is already in use. \r\nIt may already be running, or another program is taking up its port, or other programs are taking up its port.");
Application.Exit();
}
This part of the code tells us that the RemoteMouse.exe service is listening on the TCP port 1978. We now know where to connect, but how do we decode the responses from the server?
Connection phase
A little further, we find the code block which prepares the banner of the service to be sent on the socket:
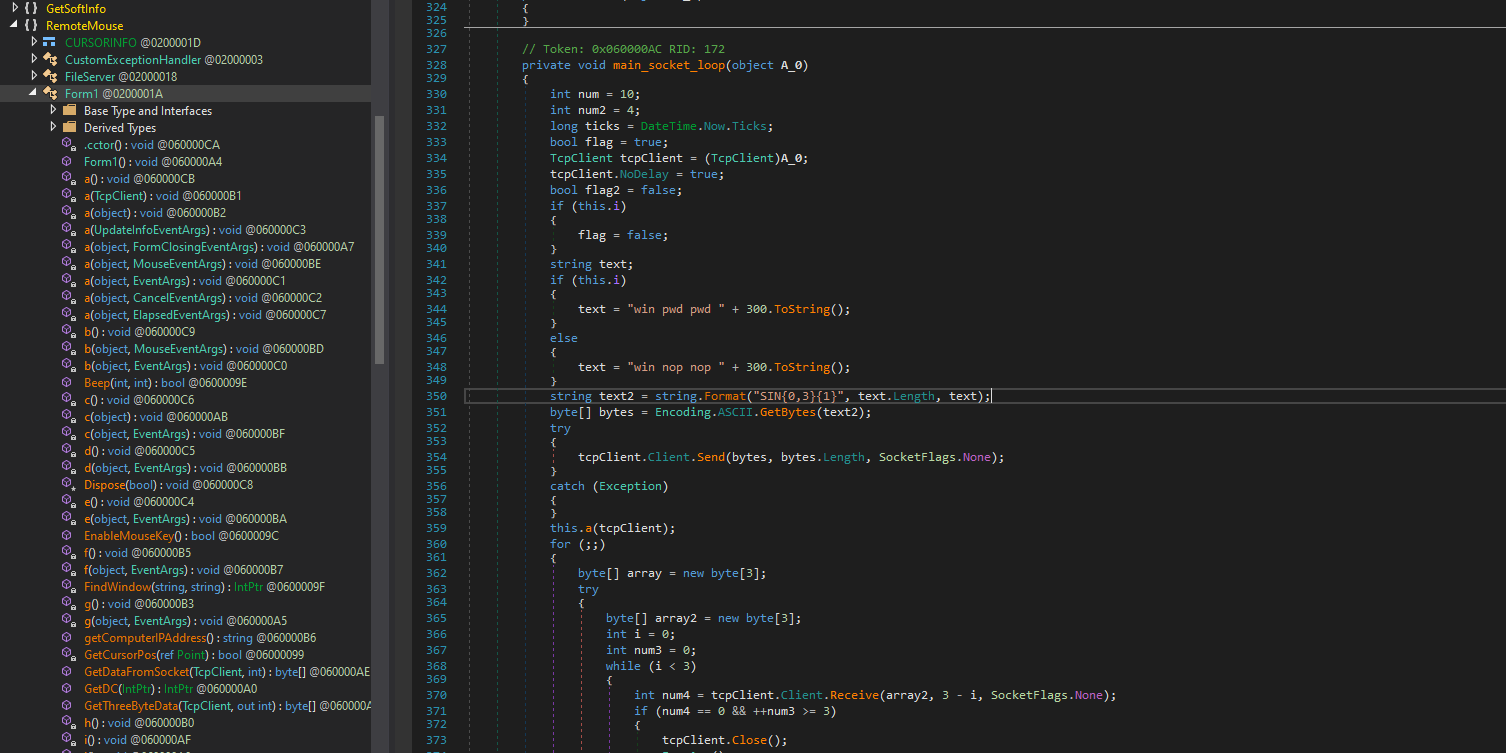
This is effectively what we see when we connect to the service via netcat:

When we connect to the RemoteMouse.exe service on the TCP port 1978, we receive one of the following two service banners:
-
SIN 15win pwd pwd 300: Indicating that the service requires authentication. -
SIN 15win nop nop 300: Indicating that the service does not require authentication.
Command interpreter
In the main loop managing the reception of data on the socket, we find this block of code allowing the interpretation of the various commands expected by the RemoteMouse service.
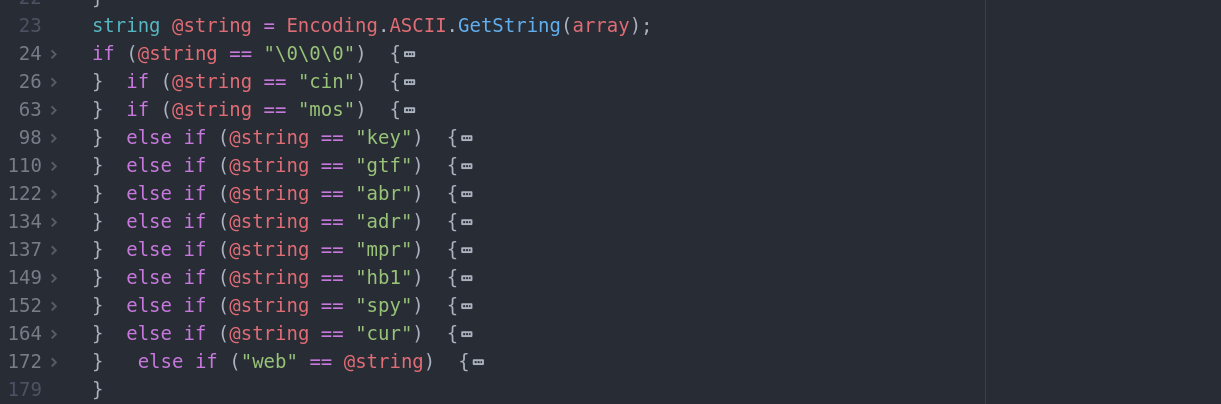
-
cin: Send password for authentication. -
mos: Mouse control. -
key: Keyboard control. -
gtf: To be defined. -
abr: To be defined. -
adr: To be defined. -
mpr: To be defined. -
hb1: To be defined. -
spy: To be defined. -
cur: To be defined. -
web: To be defined.
Demonstration
So I implemented a program to use the RemoteMouse 3.008 service to type commands on the keyboard (to implement a reverse shell for example). Here’s a full demo:
Limitations
Some fields are protected from keyboard / mouse inputs controlled by software. I noticed that this was the case on the login page of a Windows session and on the User Account Control (UAC) window. The machine targeted by this attack must therefore be unlocked.