Articles
-
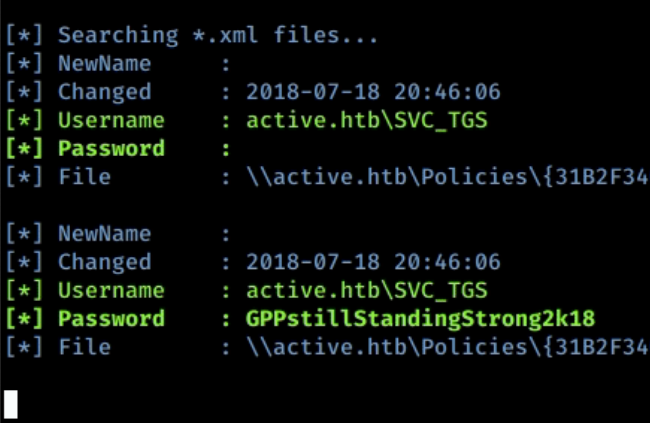 May 20, 2021Exploiting Windows Group Policy Preferences
May 20, 2021Exploiting Windows Group Policy Preferences
Group Policy Preferences (GPP) can be very dangerous if they are used to store passwords. To quickly find these in a pentest, we made a tool with Shutdown that crawls and extracts these passwords from Windows shares !May 20, 2021 Exploiting Windows Group Policy Preferences -
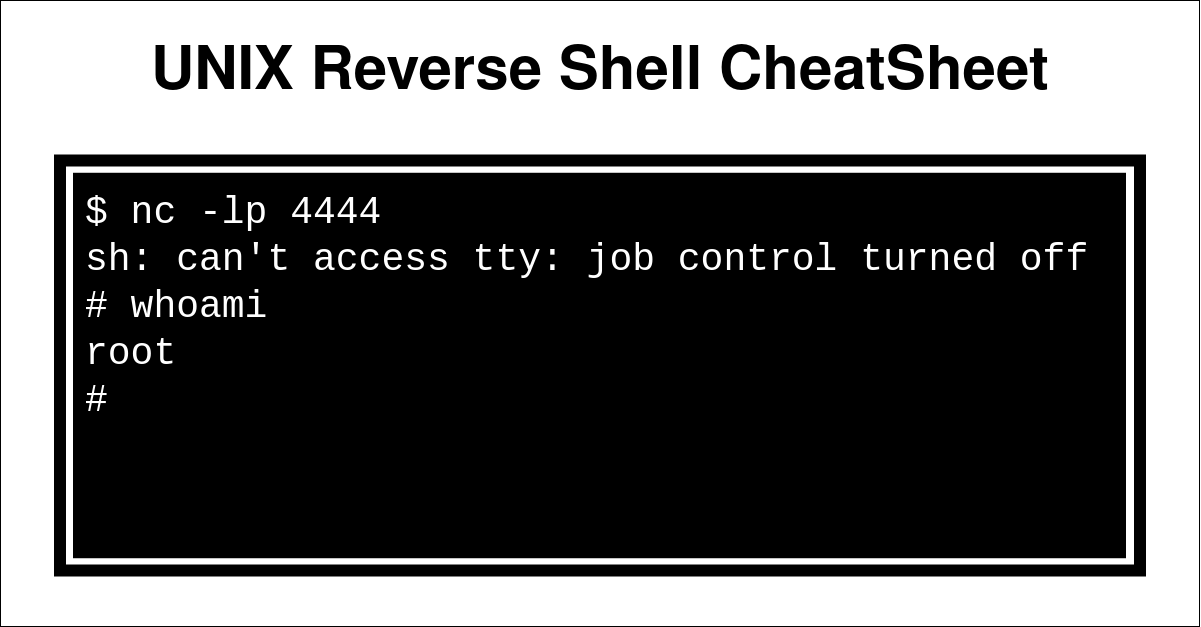 May 17, 2021UNIX Reverse Shells Cheatsheet
May 17, 2021UNIX Reverse Shells Cheatsheet
UNIX Reverse Shells : 42 payloads in 17 different languages !May 17, 2021 UNIX Reverse Shells Cheatsheet -
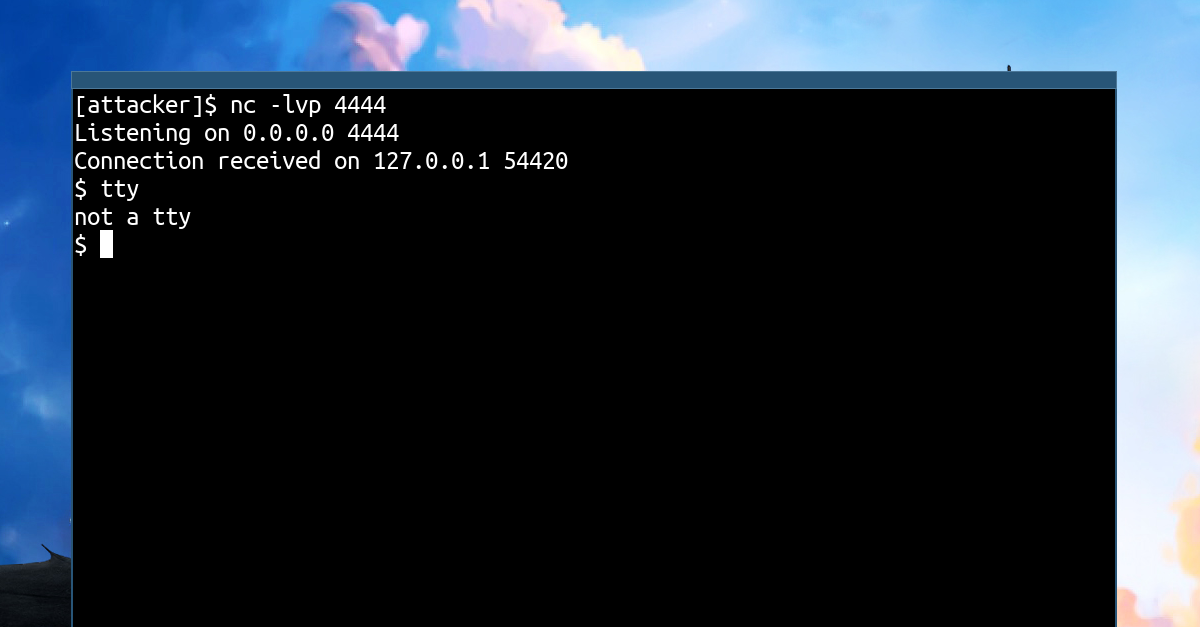
April 20, 2021 TTYs and where to find them
-
 March 24, 2021Python format string vulnerabilities
March 24, 2021Python format string vulnerabilities
Python format strings can be very useful but they can be prone to vulnerabilities when misused.March 24, 2021 Python format string vulnerabilities -
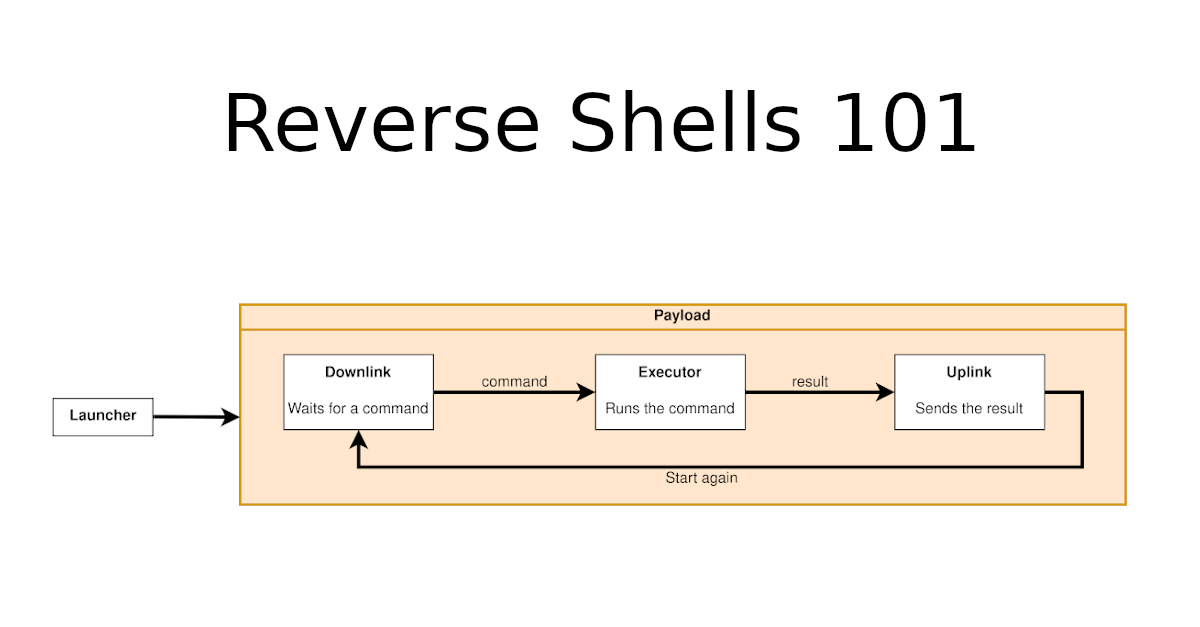 December 11, 2020Reverse Shells 101
December 11, 2020Reverse Shells 101
This article explains the necessary components to create a reverse shell.December 11, 2020 Reverse Shells 101 -
 November 12, 2020Constructing a semi-interactive reverse shell with curl
November 12, 2020Constructing a semi-interactive reverse shell with curl
This article details how I created a curl-based reverse shell, from scratch.November 12, 2020 Constructing a semi-interactive reverse shell with curl -
 November 11, 2020Constructing a semi-interactive reverse shell with wget
November 11, 2020Constructing a semi-interactive reverse shell with wget
This article details how I created a wget-based reverse shell, from scratch.November 11, 2020 Constructing a semi-interactive reverse shell with wget
Compact view