DVID Writeup 02 - Firmware - Hardcoded password
If you’re not yet familiar with the Damn Vulnerable Iot Device (DVID) project, I encourage you to read the project presentation page.
Goal of this challenge
A confidential message is stored on the firmware but protected by a password.
Flashing the board
First things first, we are going to flash the firmware for this challenge onto the DVID board. In order to do this, we will use avrdude and an USB AVR programmer. If you’re not familiar with avrdude options I encourage you to read the flashing the board section of the first DVID writeup of this series. We will flash the board using this nice flash.sh script :
#!/bin/bash
if [[ ! -d "./DVID/" ]]; then
git clone https://github.com/vulcainreo/DVID
fi
pushd ./DVID/trainings/firmware/hardcodedPassword/
avrdude -F -v -p atmega328p -P /dev/ttyUSB0 -c usbasp -u -U flash:w:hardcodedPassword.ino.with_bootloader.arduino_standard.hex
popd
Now, we will connect the DVID board to our computer using the USB AVR programmer, and start the script. When the AVR programming has completed, the board should restart and you should see this :
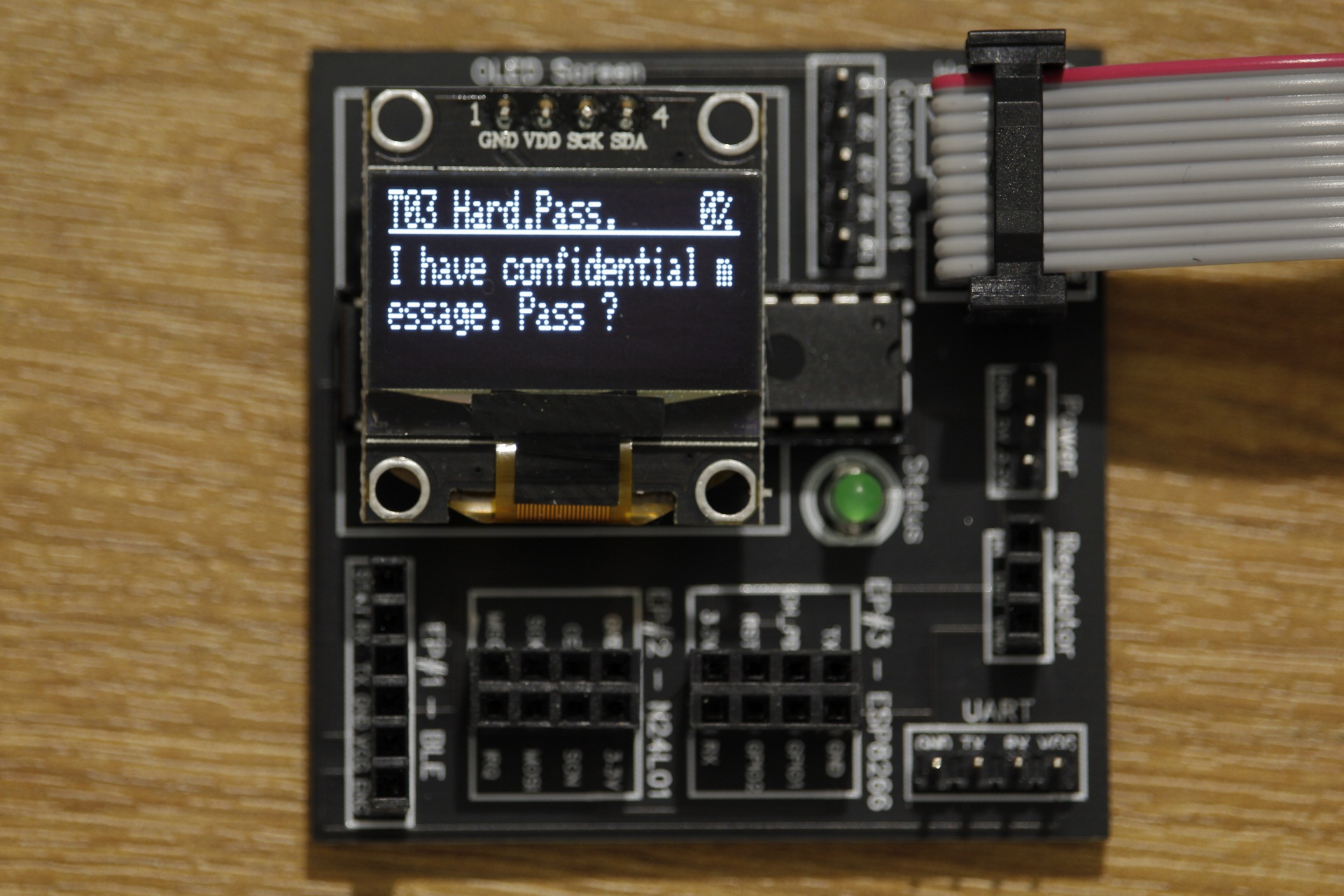
Solving the challenge : dumping the firmware
Now that we have flashed the firmware, we can start the challenge. The first step of an attacker wanting to analyze the firmware would be to try and extract it. Therefore, let’s learn how to extract it !
As we have seen in a previous article DVID Writeup 01 - Hardware - Find the Datasheet, the avrdude utility can do multiple things ! For extracting the firmware, the command differs only a little from the command to flash the firmware. We will only change the Memory operation mode in the -U option.
We used
-U flash:w:findTheDatasheet.ino.arduino_standard.hexto install the firmware on the board.We will use
-U flash:r:firmware.binto dump the firmware from the board. (We could have also dumped it in hex format with-U flash:r:firmware.hex)
The command becomes :
avrdude -F -v -p atmega328p -P /dev/ttyUSB0 -c usbasp -u -U flash:r:firmware.bin
Now that we have our extracted firmware in binary format, let’s try something simple. The strings command can be used to extract ASCII strings from the raw binary file, which is a pretty useful first step in reversing something.
strings -a firmware.bin
And in the extracted strings, we find some interesting informations :
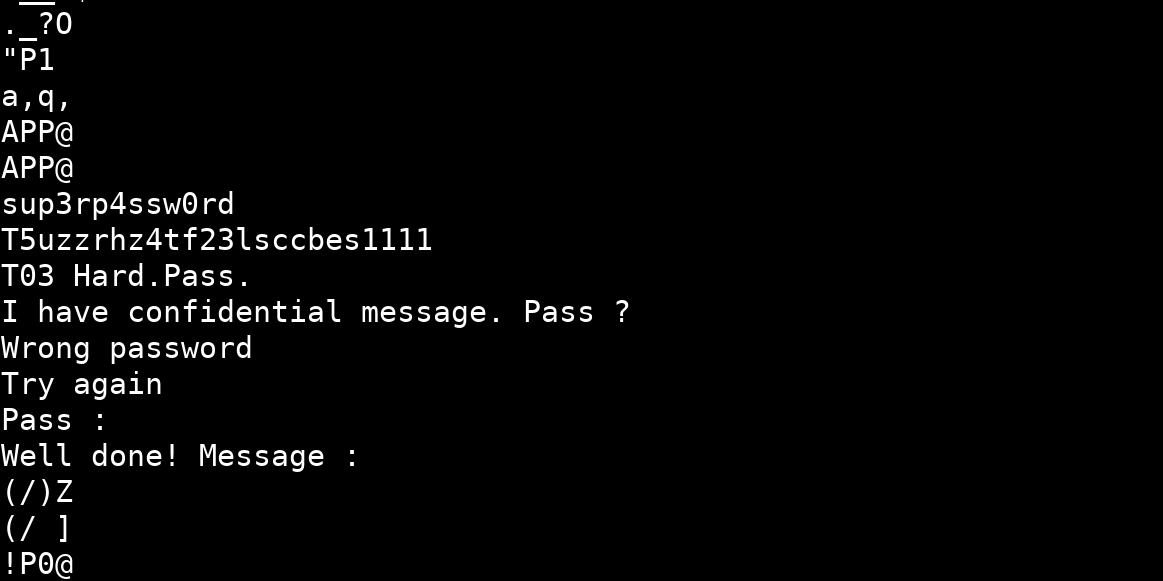
Now that we have the password, we can send it to the DVID board using the UART USB reader and this python script :
#!/usr/bin/env python3
import serial
s = serial.Serial("/dev/ttyUSB0", 9600)
s.write(b'sup3rp4ssw0rd\r\n')
We now check the screen on the DVID board :

And we won !
We also could have solved the challenge by analyzing the firmware source code.
Solving the challenge : analyzing the firmware source code
We also could have solved the challenge another way if we consider we can access the firmware source code. In this case, we can look for hardcoded variables in the code of the file hardcodedPassword.ino :
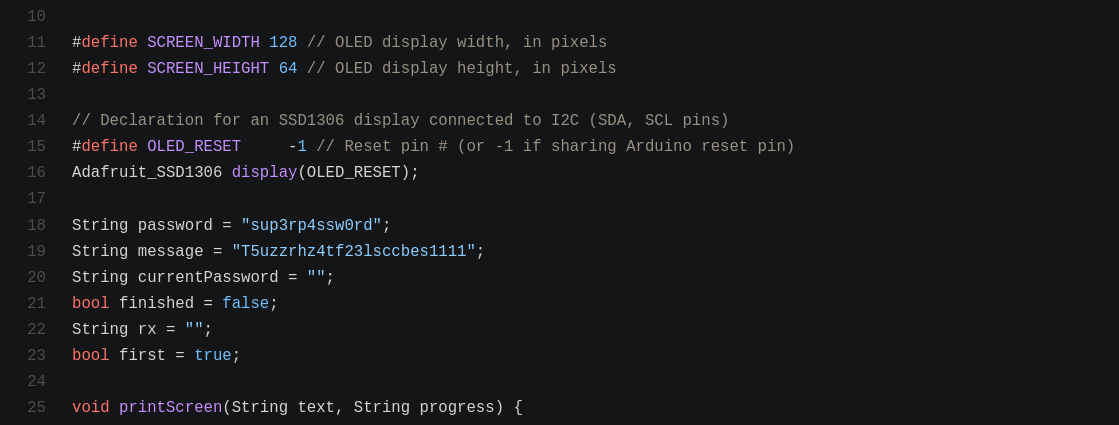
We easily find the hardcoded password on line 18 of the file hardcodedPassword.ino. Of course, the idea here is to learn about realistic attacks, you might not always have the source code of the firmware !
Additional references
- DVID Project on Github : https://github.com/Vulcainreo/DVID
- DVID Project site : http://dvid.eu/
- https://blog.rapid7.com/2019/04/16/extracting-firmware-from-microcontrollers-onboard-flash-memory-part-1-atmel-microcontrollers/