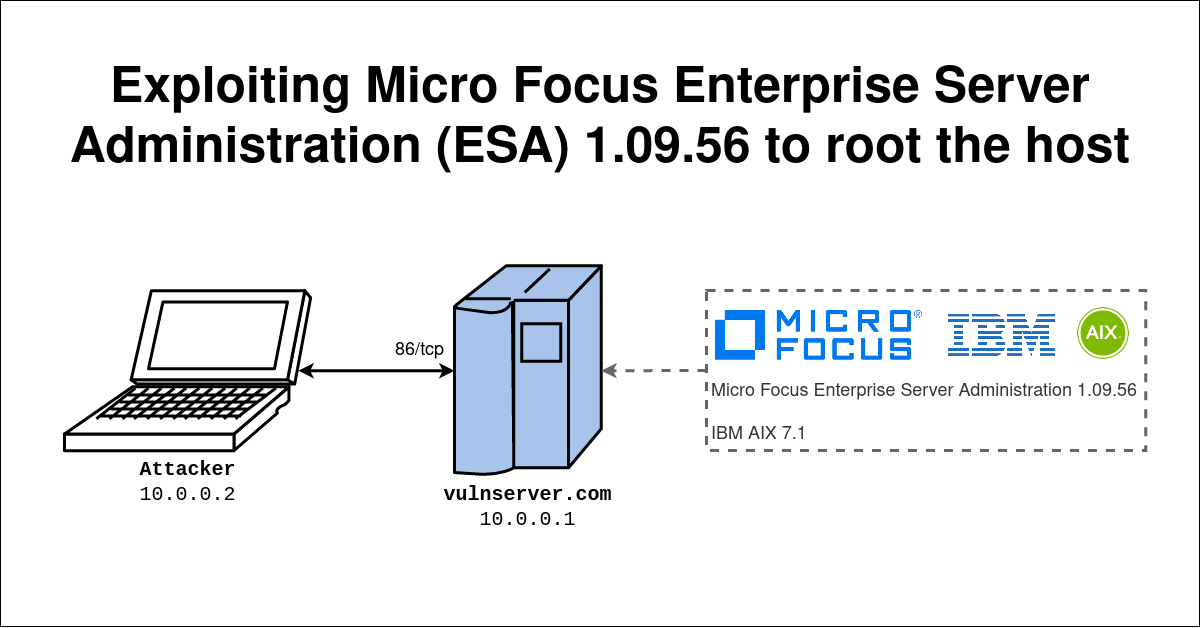
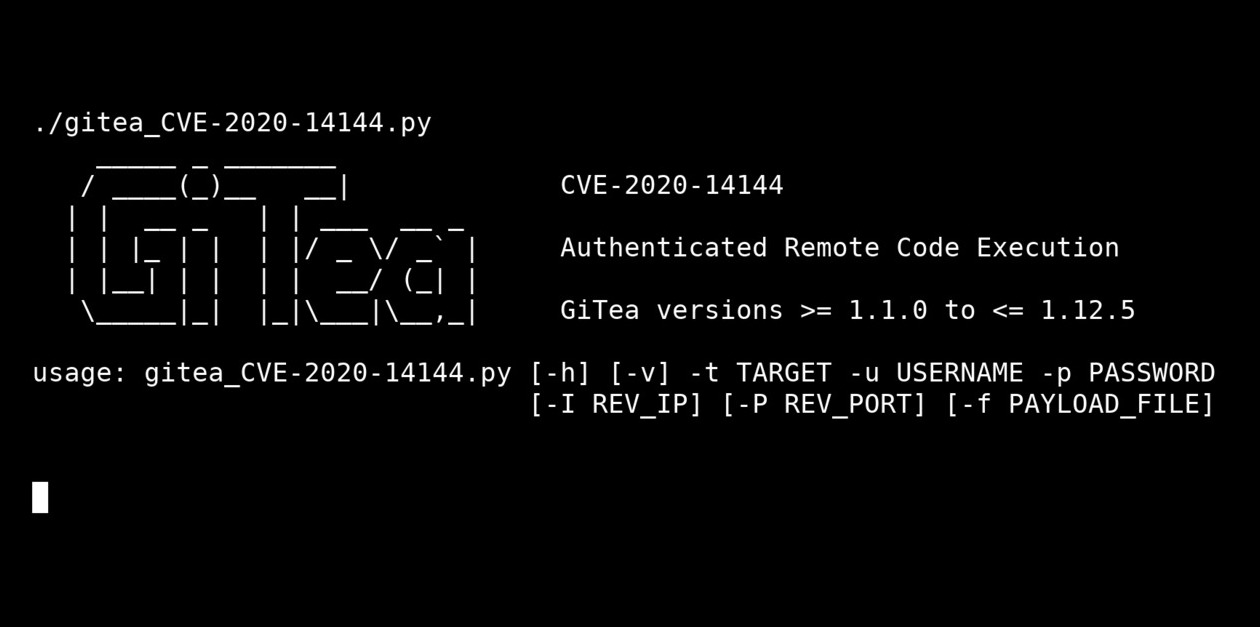
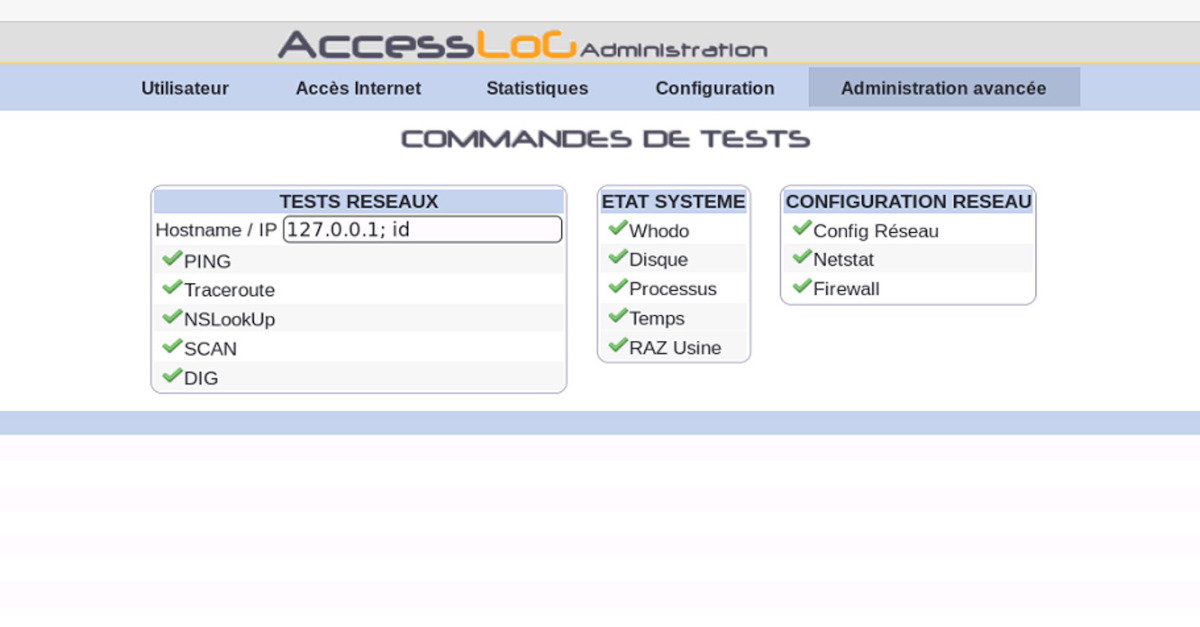
Python vulnerabilities : Code execution in jinja templates
July 27, 2022
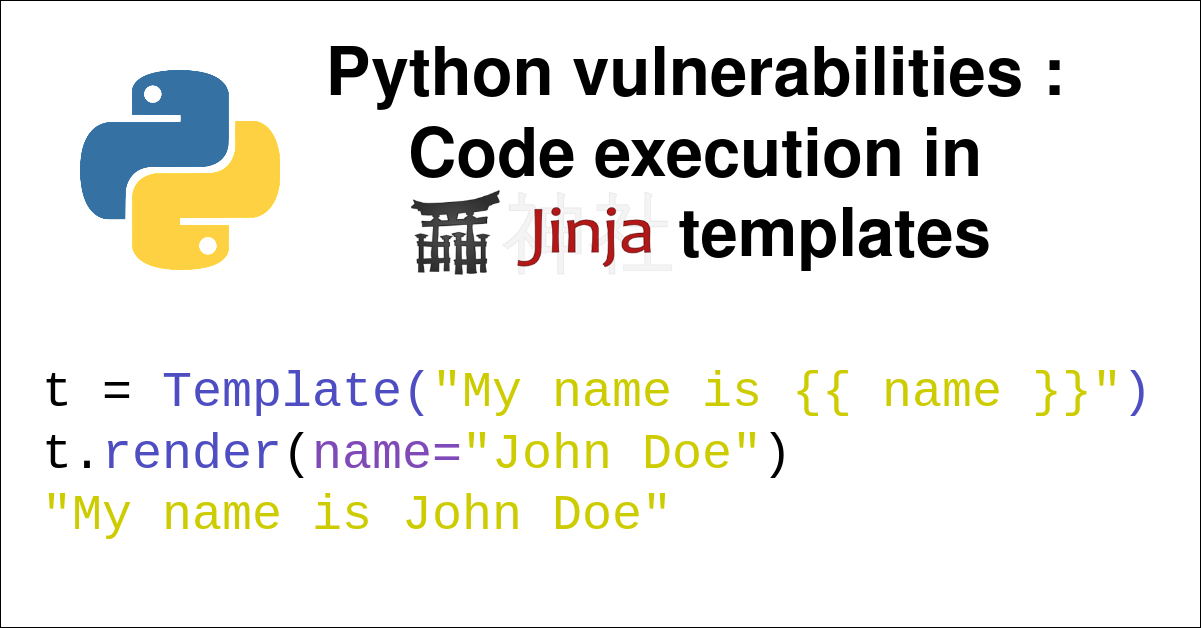
We will see how to create context-free payloads for jinja2, always allowing direct access to the os module in a jinja2 template without requirements. These payloads will be particularly useful for exploiting SSTI vulnerabilities.