SSH Port forwarding
Introduction
During pentesting, in Capture The Flag, or simply for system administration, we may need to access ports on remote machines or remote networks.
In order to do this, we use a technique called “port forwarding” allowing access to previously unreachable ports. This technique can notably be useful to access services which run locally on the server (services listenning on 127.0.0.1 for example) in a secure manner without opening ports outside the machine. In this article, we’ll take a look at port forwarding with SSH.
Port forwarding with SSH
To fully understand the direction in which SSH redirects are made, wee need to look at the point of view of the client from which you are connecting in SSH. So we have :
-
Local forwarding: Forwards a given port on the server to which we connect in SSH to the client. We use this type of port forwarding when we want to access a port on the SSH connection server to which we connect, but which we cannot access (because of a firewall, a listen on
127.0.0.1, …). -
Remote forwarding: Forwards a port of the SSH client or a remote machine to the server of the SSH connection. This type of port forwarding is used to expose a port from the client machine to the remote server. (To access multiple ports/machines on the remote network, it is better to use dynamic port-forwarding)
We will see in the following sections examples of different types of redirects, based on this test network:
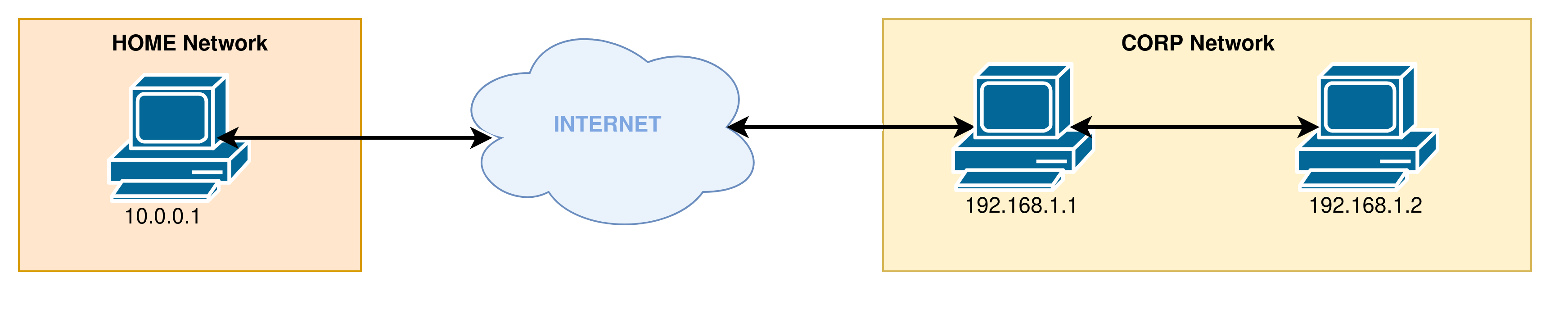
In this network, the machine 192.168.1.1 and its SSH port 22 of the CORP network are publicly accessible on the domain name remote.corp.com.
Local port forwarding
Local port forwarding allows a client machine to access an open port on the SSH connection server, or a port on a machine that the SSH server can contact on the network. To perform local port forwarding, the syntax of the SSH command is as follows:
ssh -L [bind_address:]my_local_port:destination_ip:remoteserver_local_port user@remoteserver
Here are the details of the options of this command:
-
-L: Specify a local port forwarding, this option expects a forwarding path, which we will see shortly after. -
[bind_address:]my_local_port:destination_ip:remoteserver_local_port: This is the redirect path. It specifies the local port to open on the client machine of the SSH connection, as well as the IP and the remote port to redirect. It is possible to specify on which local address on the client machine the port will be opened (it is thebind_address). By default thebind_addressis set to the local address127.0.0.1. It is also possible to connect to machines belonging to the SSH server network by specifying the machine’s IP in thedestination_ipfield under this option. -
user@remoteserver: This element corresponds to the user and the remote server with which the SSH connection will be established.
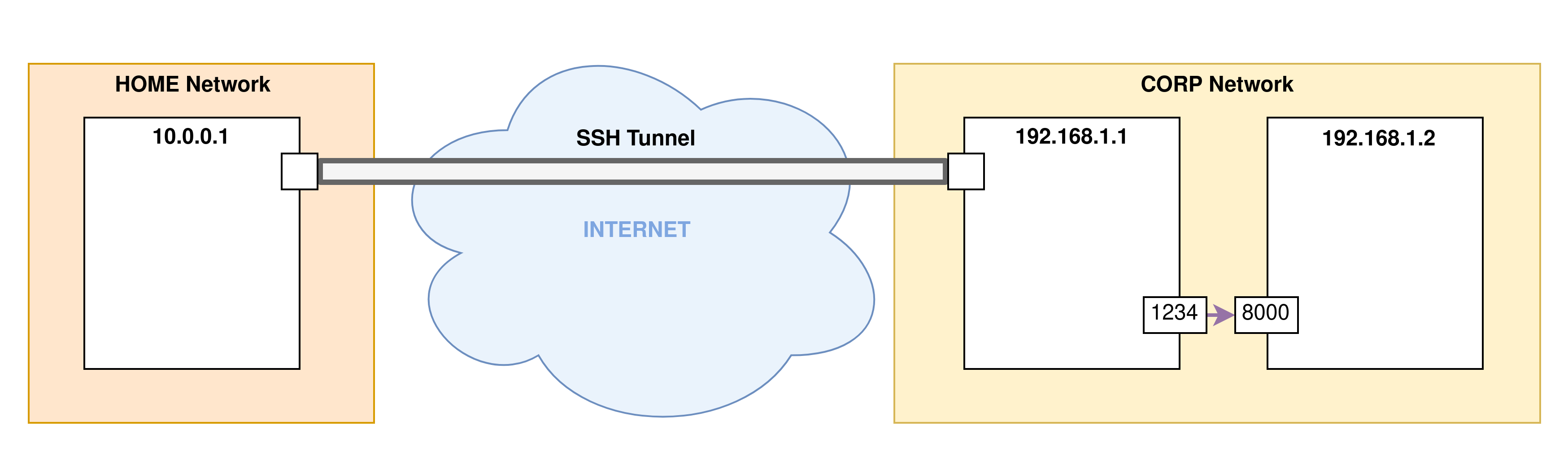
Let’s see a practical example of local port forwarding in our test network:
Example 1
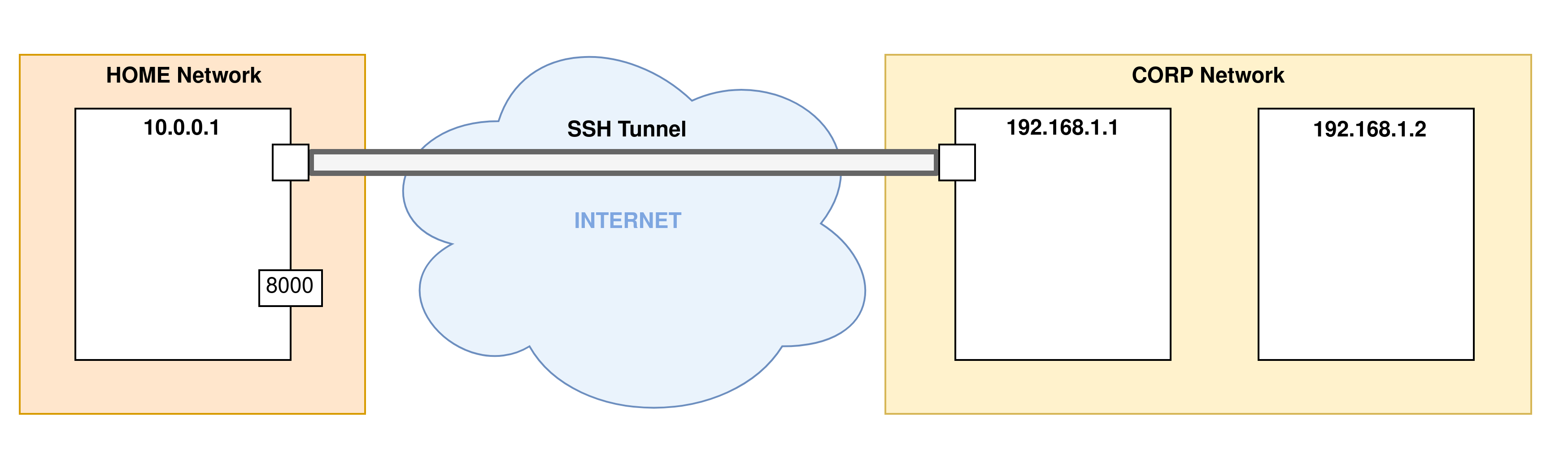
In this example we are going to redirect the local port 8000 of the machine 192.168.1.1 to the port 1234 of our machine via SSH. The command is therefore the following:
ssh -L 1234:127.0.0.1:8000 user@remote.corp.com
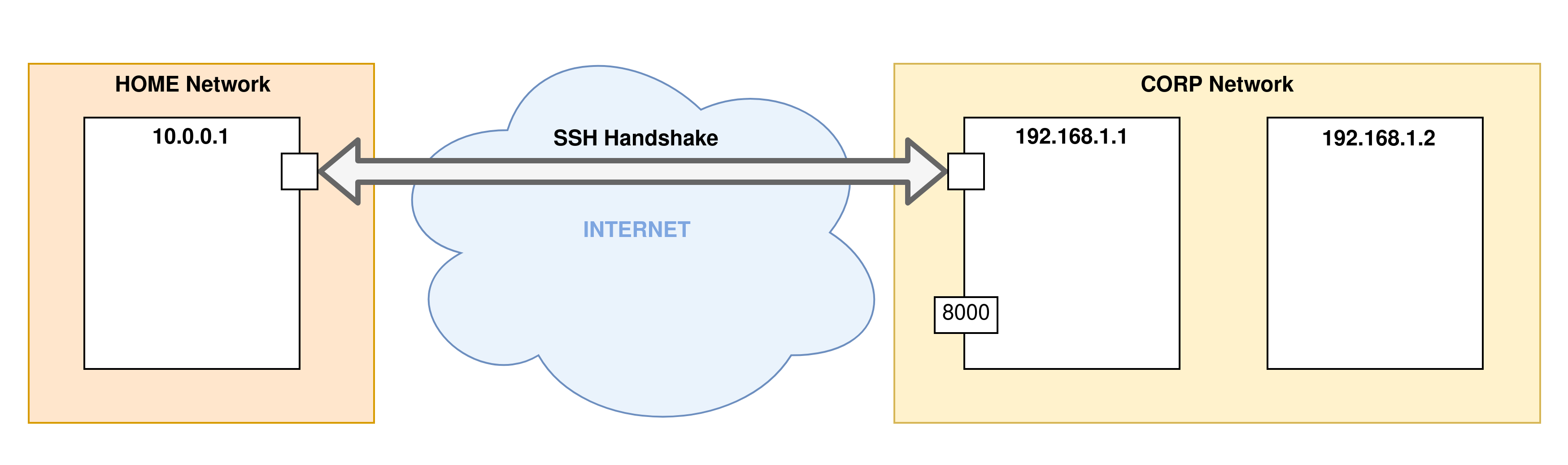
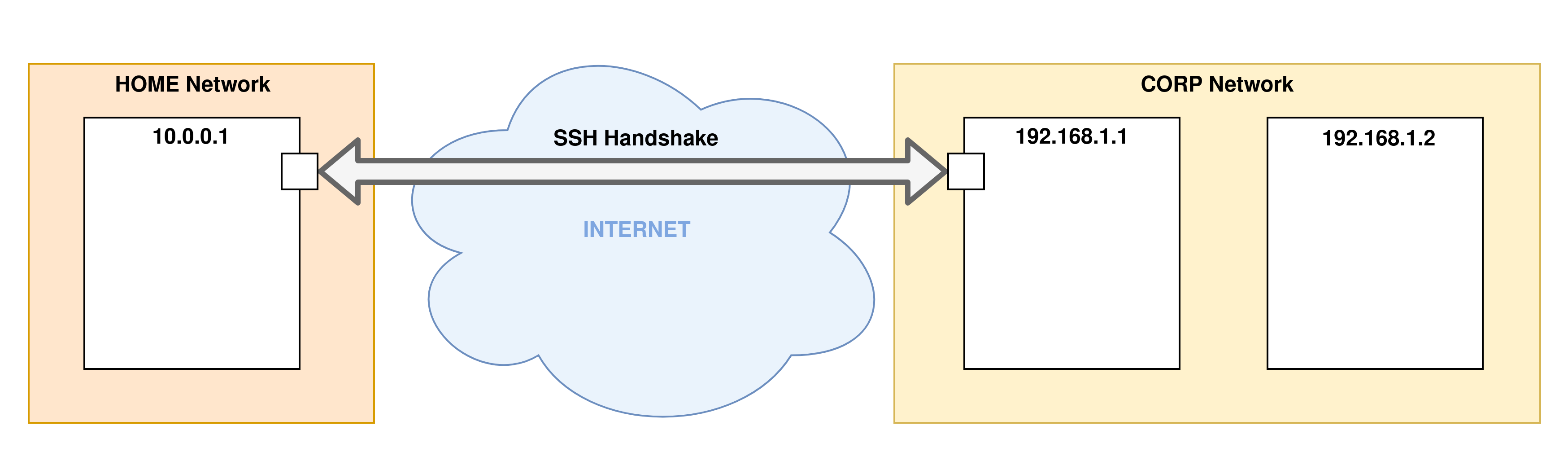
- Step 1: The first step is the phase of establishing an SSH connection to the remote server. This is when the SSH tunnel is established:
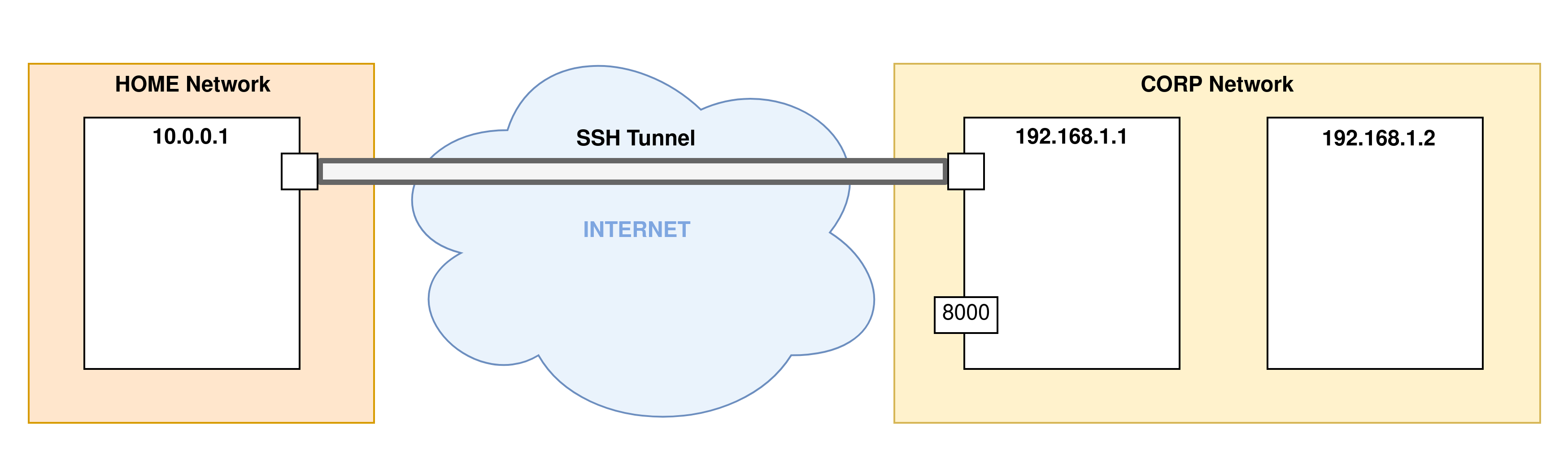
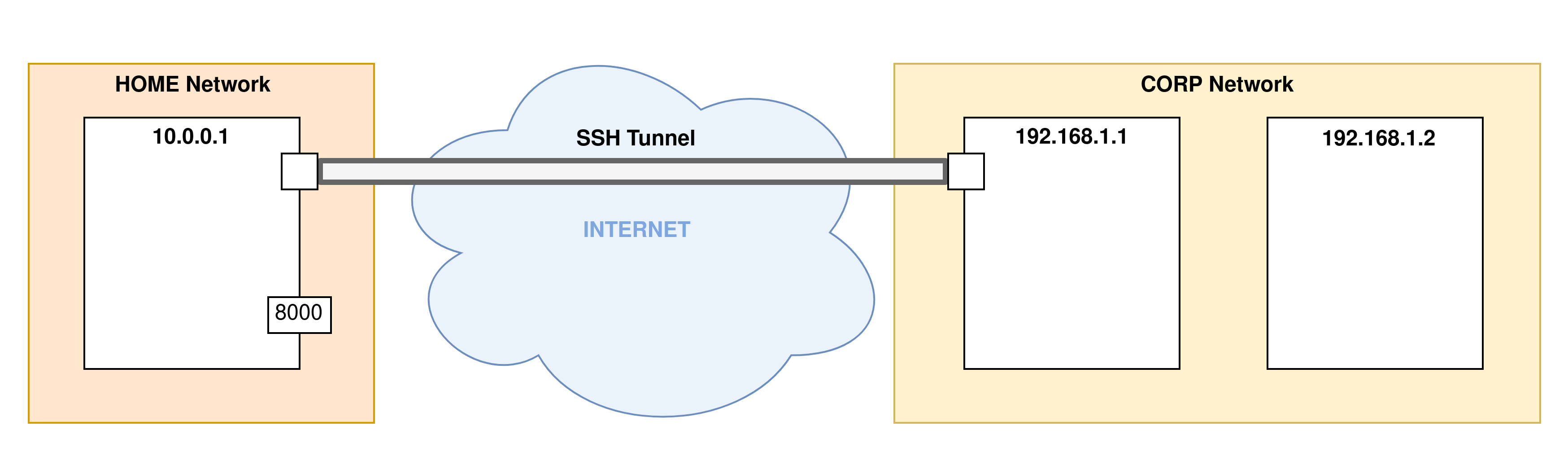
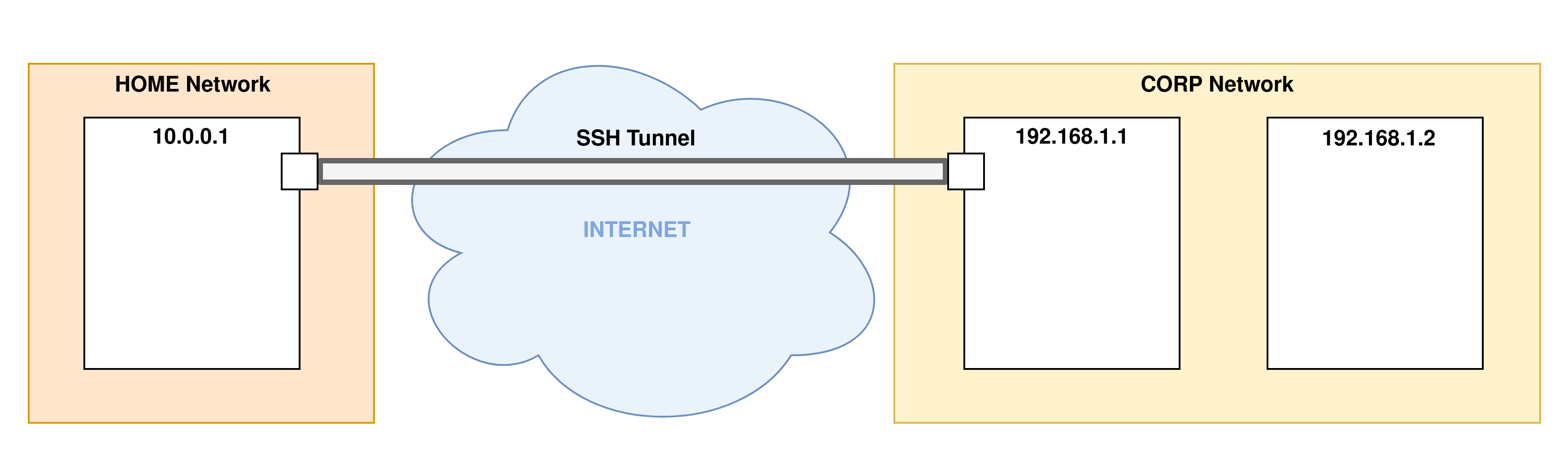
- Step 2: When the SSH connection establishment phase is finished, the tunnel is in place and ready to process the port forwarding options:
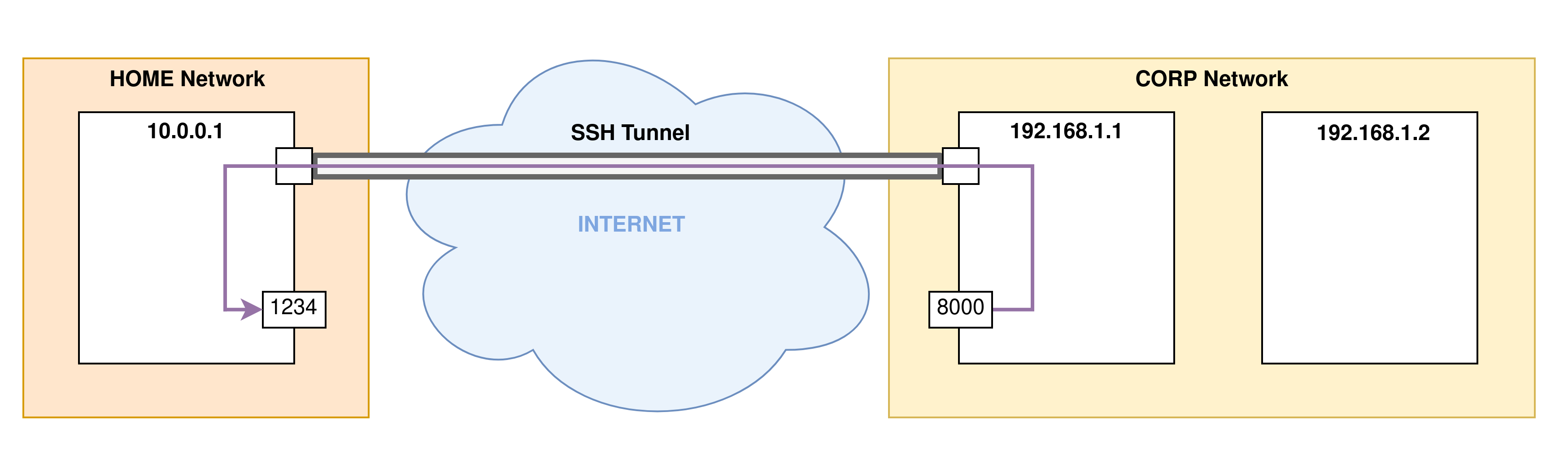
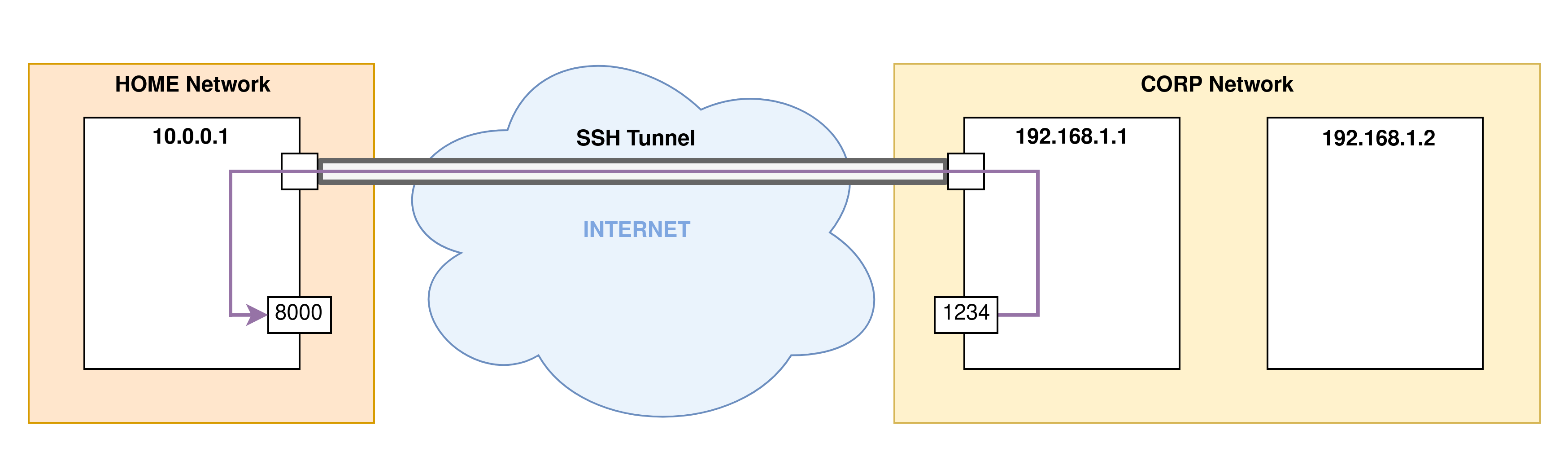
- Step 3: Port forwarding will now begin. Here the port
8000of the remote machine (the SSH server) is forwarded to the port1234on the client machine of the SSH connection:
Remote port forwarding
Remote port forwarding allows a client machine of an SSH connection to redirect one of its ports to a port on the server, or to redirect a port of a network machine from the SSH server to a port local to the server. This can be useful for accessing services that run on machines in the server’s network in a secure manner without opening ports to the outside the network.
To perform a remote port forwarding, the syntax of the SSH command is as follows:
ssh -R [bind_address:]my_local_port:remote_ip:remoteserver_local_port user@remoteserver
Here are the details of the options of this command:
-
-R: Specify remote port forwarding, this option expects a forwarding path, which we will see shortly after. -
[bind_address:]my_local_port:remote_ip:remoteserver_local_port: This is the redirect path. It specifies the local port to open on the SSH connection server, as well as the IP and remote port to redirect. It is also possible to specify on which local address of the server the port will be opened (this is thebind_address). By default this address is set to127.0.0.1. -
user@remoteserver: This element corresponds to the user and the remote server with which the SSH connection will be established.
Let’s see a practical example of remote port forwarding in our test network:
Example 2
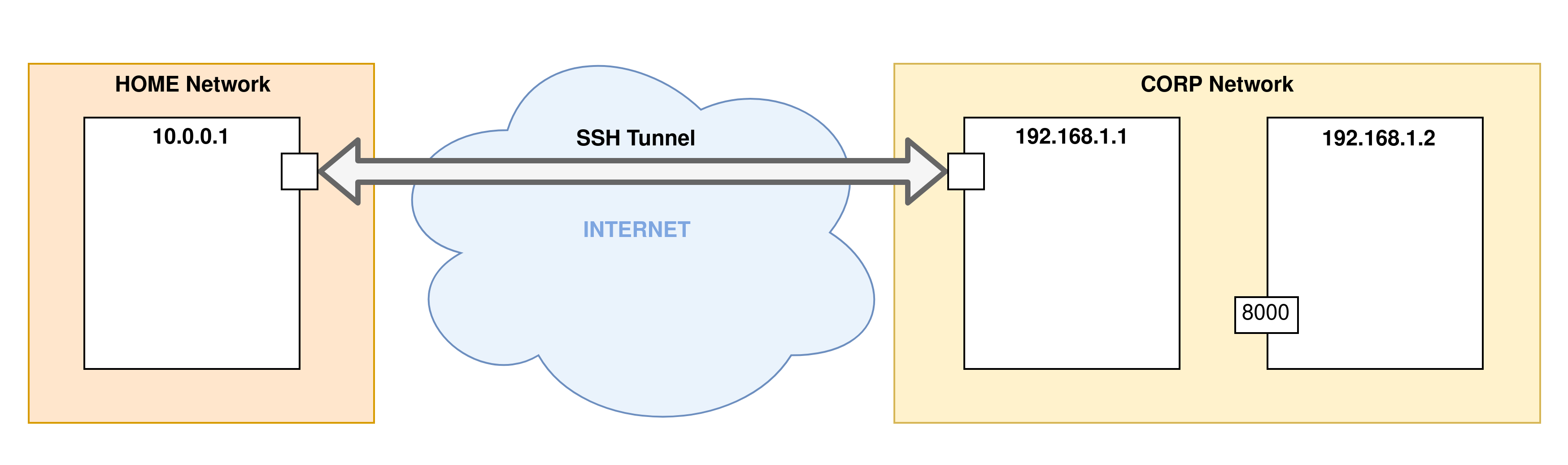
In this example we are going to redirect the remote port 8000 of the machine 192.168.1.2 to the local port 1234 of the server 192.168.1.2 via SSH.
ssh -R 1234:192.168.1.2:8080 user@192.168.1.1
- Step 1: The first step is the phase of establishing an SSH connection to the remote server. This is when the SSH tunnel is established:
- Step 2: When the SSH connection establishment phase is finished, the tunnel is in place and ready to process the port forwarding options:
- Step 3: Port forwarding will now begin. Here the port
8000of the client machine of the SSH connection is forwarded to the port1234of the server of the SSH connection:
Exemple 3
Here is another example allowing to redirect the port 8000 of the machine 192.168.1.2 to the port 1234 of the server of the SSH connection:
ssh -R 192.168.1.1:1234:192.168.1.2:8000 user@192.168.1.1
- Step 1: The first step is the phase of establishing an SSH connection to the remote server. This is when the SSH tunnel is established:
- Step 2: When the SSH connection establishment phase is finished, the tunnel is in place and ready to process the port forwarding options:
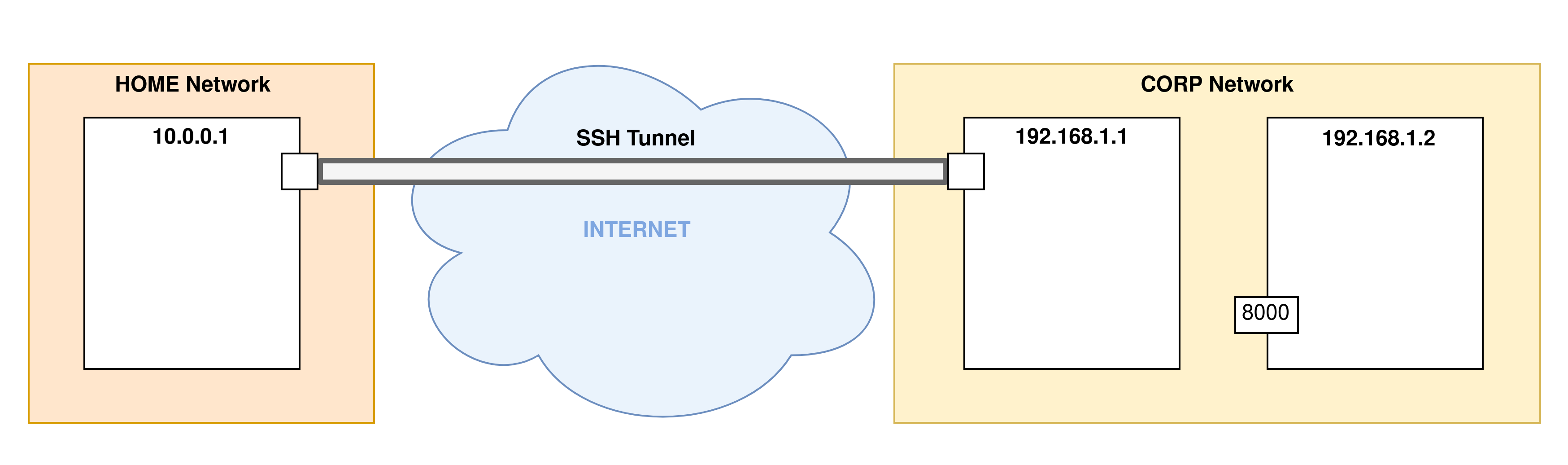
- Step 3: Port forwarding will now begin. Here the port
8000of the remote machine belonging to the server network is redirected to the port1234on the server of the SSH connection:
Dynamic port forwarding
Thanks to the ssh command it is also possible to perform dynamic port forwardings. To do this, during an SSH connection configured to perform this type of redirects, a port is opened on the client machine of the SSH connection to host a SOCKS proxy. Then we can use this proxy to connect to ports on the remote machine.
To initiate dynamic port forwarding, use the ssh command with the -D argument followed by the local port that will host the SOCKS proxy on your client machine:
ssh -D local_port user@remoteserver
Example 3
The following command is used to connect in SSH to the remote machine remote.corp.com ( 192.168.1.1) then to launch a SOCKS proxy on your local machine on port 8080:
ssh -D 8080 user@remote.corp.com
- Step 1: The first step is the phase of establishing an SSH connection to the remote server. This is when the SSH tunnel is established:
- Step 2: When the SSH connection establishment phase is finished, the tunnel is in place and ready to process the port forwarding options:
- Step 3: Port redirects are set up. Here a SOCKS proxy is open on port
8080of the client machine of the SSH connection. This proxy allows you to make requests on any machine / ports belonging to the network of the remote server:
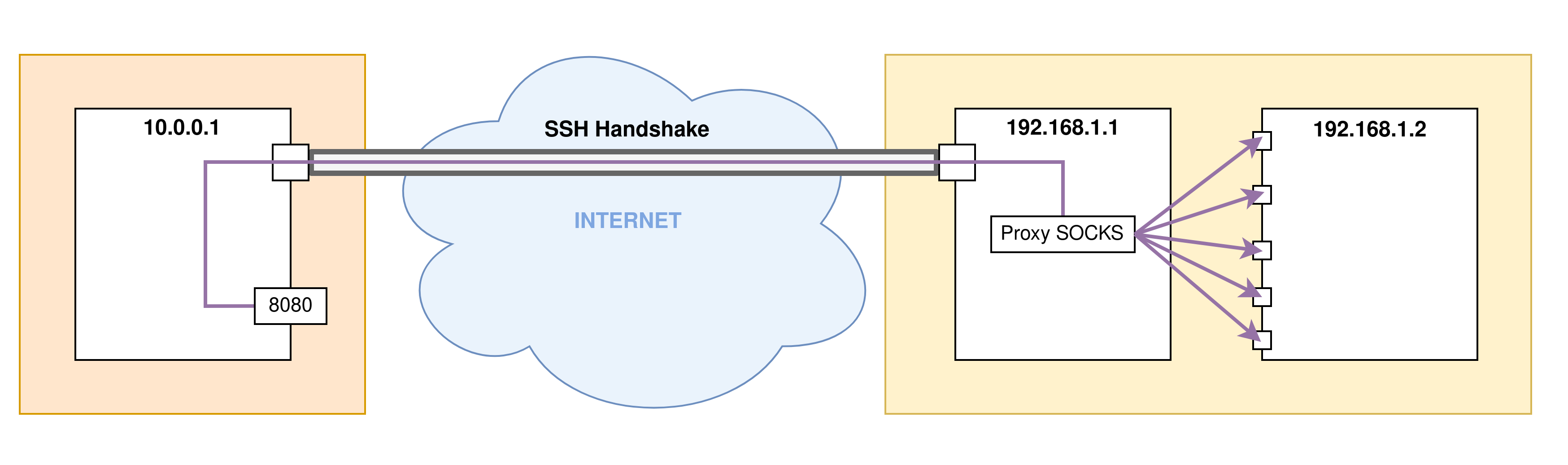
Then we can use this proxy in various tools to access the remote internal network of CORP.